Continuous Monitoring Plan Template
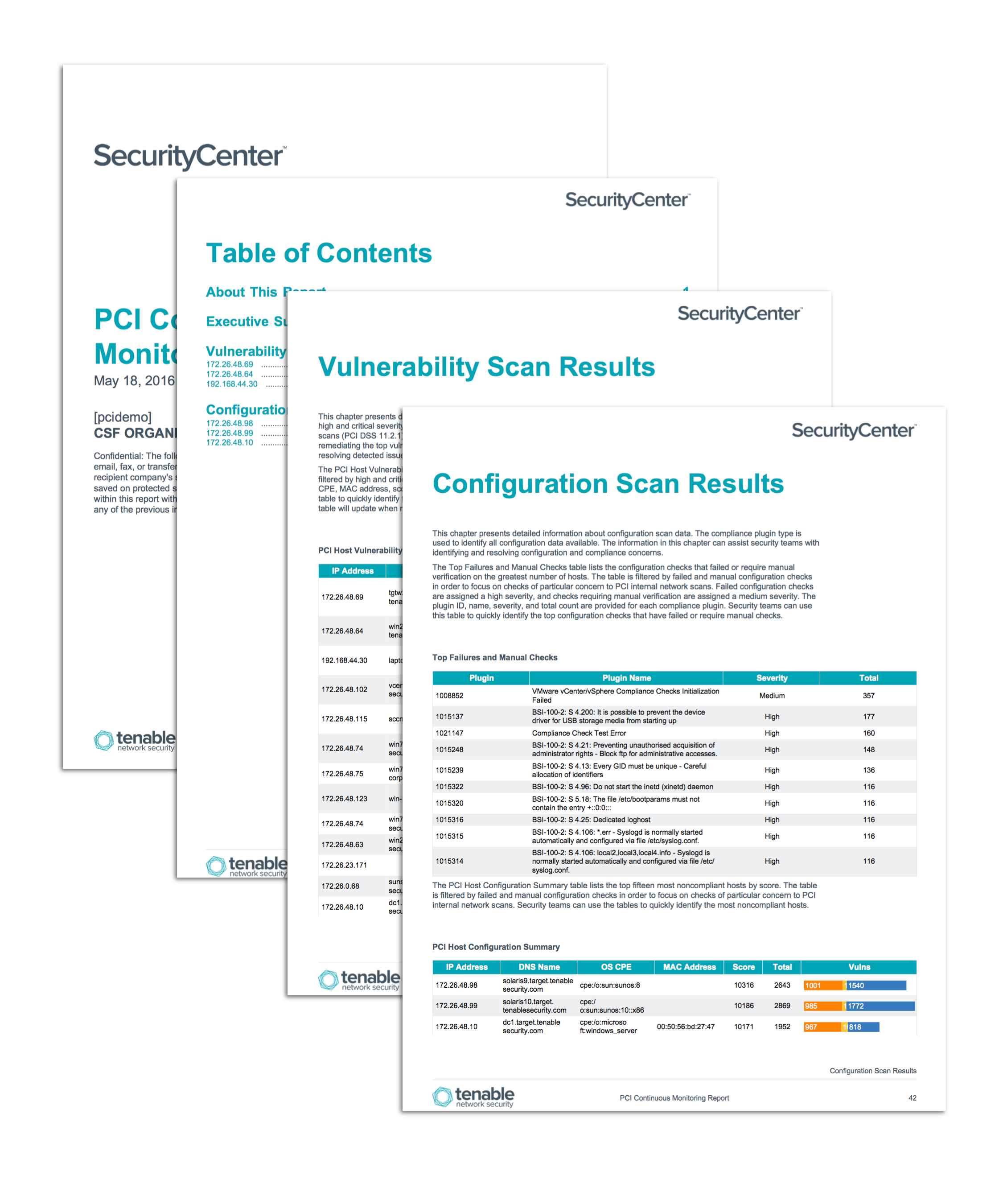
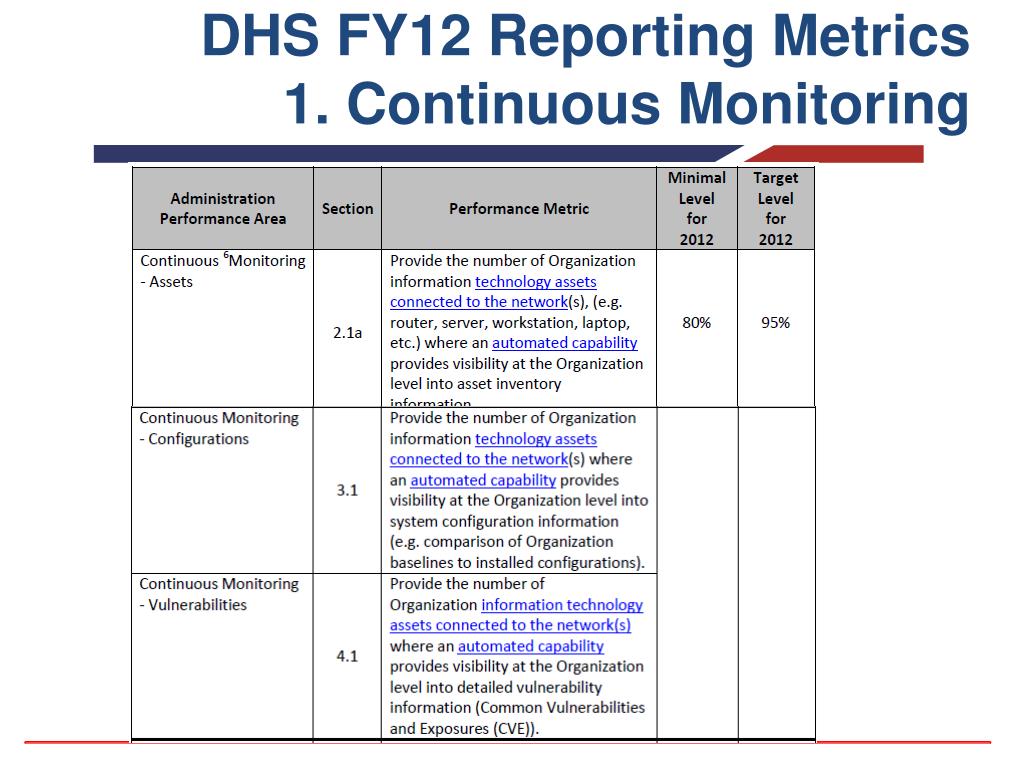
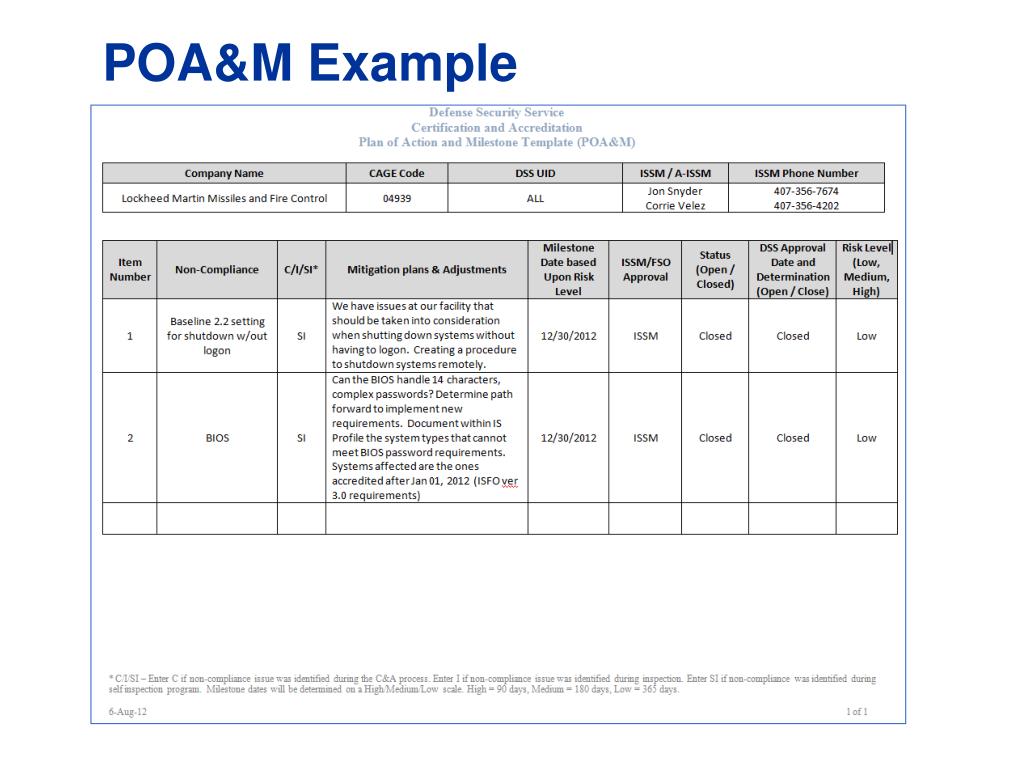
Continuous Monitoring Plan Template - Web information system continuous monitoring (iscm) plan. It was developed directly from nist guidance and is applicable to any organization, public or private. The poa&m is a key document in the security authorization package and monthly continuous monitoring activities. Ongoing due diligence and review of security controls enables the security. Web this document provides guidance on continuous monitoring and ongoing authorization in support of maintaining a security authorization that meets the federal. Web continuous monitoring (iscm) program. Web continuous monitoring is used to make recurring updates to the security assessment package. This document provides guidance on continuous monitoring and ongoing authorization in support of maintaining a security authorization. Web the fedramp poa&m template. Web this continually monitoring plan (cmp) has been prepared to support assessment of the ongoing security posture of of protected utility blueprint desktop environment. Use this simple contingency plan template to help your organization return to daily operations after unforeseen. Web about this document. Web abstract this publication describes an example methodology for assessing an organization's information security continuous monitoring (iscm) program. Web nistir 8212, an information security continuous monitoring program assessment, provides an operational approach to the assessment of an organization’s. Web information. It can be used as documented or. Web continuous monitoring (iscm) program. Web continuous monitoring is used to make recurring updates to the security assessment package. Web about this document. Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring. This document provides guidance on continuous monitoring and ongoing authorization in support of maintaining a security authorization. Personally, i'd make two separate documents but. Web the fedramp poa&m template provides a structured framework for aggregating system vulnerabilities and deficiencies through security assessment and continuous monitoring. Ongoing due diligence and review of security controls enables the security. It can be used. Use this simple contingency plan template to help your organization return to daily operations after unforeseen. This publication describes an approach for the development of information security continuous monitoring (iscm) program assessments that can be. Web abstract this publication describes an example methodology for assessing an organization’s information security continuous monitoring (iscm) program. Web this continually monitoring plan (cmp) has. Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring. Personally, i'd make two separate documents but. Web simple contingency plan template. Web abstract this publication describes an example methodology for assessing an organization's information security continuous monitoring (iscm) program. Web about this document. This publication describes an approach for the development of information security continuous monitoring (iscm) program assessments that can be. Web continuous monitoring (iscm) program. Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring. Web on c&a activities what is continuous monitoring? Web continuous monitoring. Web abstract this publication describes an example methodology for assessing an organization's information security continuous monitoring (iscm) program. Web information system continuous monitoring (iscm) plan. Ongoing due diligence and review of security controls enables the security. The poa&m is a key document in the security authorization package and monthly continuous monitoring activities. Web the fedramp poa&m template. Web about this document. Web continuous monitoring (iscm) program. It was developed directly from nist guidance and is applicable to any organization, public or private. Web this continually monitoring plan (cmp) has been prepared to support assessment of the ongoing security posture of of protected utility blueprint desktop environment. Web continuous monitoring pdf continuous monitoring escalation process this document explains. Use this simple contingency plan template to help your organization return to daily operations after unforeseen. Web abstract this publication describes an example methodology for assessing an organization's information security continuous monitoring (iscm) program. The poa&m is a key document in the security authorization package and monthly continuous monitoring activities. Web continuous monitoring pdf continuous monitoring escalation process this document. Web information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational. Web the fedramp poa&m template provides a structured framework for aggregating system vulnerabilities and deficiencies through security assessment and continuous monitoring. Web abstract this publication describes an example methodology for assessing an organization's information security continuous monitoring (iscm) program.. Web continuous monitoring (iscm) program. Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring. Web this document provides guidance on continuous monitoring and ongoing authorization in support of maintaining a security authorization that meets the federal. Ongoing due diligence and review of security controls enables the security. Web the fedramp poa&m template provides a structured framework for aggregating system vulnerabilities and deficiencies through security assessment and continuous monitoring. Web abstract this publication describes an example methodology for assessing an organization’s information security continuous monitoring (iscm) program. Web continuous monitoring is used to make recurring updates to the security assessment package. Web on c&a activities what is continuous monitoring? This publication describes an approach for the development of information security continuous monitoring (iscm) program assessments that can be. Use this simple contingency plan template to help your organization return to daily operations after unforeseen. Web information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational. The poa&m is a key document in the security authorization package and monthly continuous monitoring activities. Web nistir 8212, an information security continuous monitoring program assessment, provides an operational approach to the assessment of an organization’s. It was developed directly from nist guidance and is applicable to any organization, public or private. Web information system continuous monitoring (iscm) plan. This document provides guidance on continuous monitoring and ongoing authorization in support of maintaining a security authorization. Web about this document. Web this continually monitoring plan (cmp) has been prepared to support assessment of the ongoing security posture of of protected utility blueprint desktop environment. It can be used as documented or. Web the fedramp poa&m template. This document provides guidance on continuous monitoring and ongoing authorization in support of maintaining a security authorization. Web simple contingency plan template. Web information system continuous monitoring (iscm) plan. The poa&m is a key document in the security authorization package and monthly continuous monitoring activities. Ongoing due diligence and review of security controls enables the security. It can be used as documented or. Web continuous monitoring is used to make recurring updates to the security assessment package. Web information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational. Web the fedramp poa&m template. Web continuous monitoring (iscm) program. Web nistir 8212, an information security continuous monitoring program assessment, provides an operational approach to the assessment of an organization’s. Web this document provides guidance on continuous monitoring and ongoing authorization in support of maintaining a security authorization that meets the federal. Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring. Use this simple contingency plan template to help your organization return to daily operations after unforeseen. Web the fedramp poa&m template provides a structured framework for aggregating system vulnerabilities and deficiencies through security assessment and continuous monitoring. Web about this document.PCI Continuous Monitoring Report SC Report Template Tenable®
Continuous Monitoring FedRAMP Compliance
Action Plan (Apple iWork Pages/Numbers)
PPT Information System Continuous Monitoring (ISCM) PowerPoint
Rmf Continuous Monitoring Plan Template
TEMPLATE Continuous Monitoring Plan (ConMon) ⋆ The Cyber Sentinel
CONTRACT MONITORING PLAN
Rmf Continuous Monitoring Plan Template Master of Documents
Progressive continuous monitoring plan to terminate cyber risks
Continuous Monitoring PPT Analytics design, Powerpoint presentation
This Publication Describes An Approach For The Development Of Information Security Continuous Monitoring (Iscm) Program Assessments That Can Be.
Web On C&A Activities What Is Continuous Monitoring?
Web Abstract This Publication Describes An Example Methodology For Assessing An Organization’s Information Security Continuous Monitoring (Iscm) Program.
Personally, I'd Make Two Separate Documents But.
Related Post: