Cyber Security Meeting Agenda Template
Cyber Security Meeting Agenda Template - Send an agenda to the security team and other interested parties 3 to 5 days before the. Web ready up the discover is best tips for an effective, efficient meeting. Download free meeting agenda templates Cybersecurity and infrastructure securing agency. What every executive needs to know. Web after a cybersecurity incident • hold a formal retrospective meeting (sometimes called a “postmortem”). The agenda for the meetings or conference calls can be anything from general topics or very detailed agenda items. The agenda should be communicated to all committee members. Web november 02, 2021. The purpose of this document is to provide a framework that acts as a reference for the florida courts to assist them with establishing local policies, technical. Web we collected 40+ meeting agenda templates to make your meetings more effective and productive! Cybersecurity best practices, organizations and cyber safety, cyber threats and advisories. Web prepare the meeting agenda. The purpose of this document is to provide a framework that acts as a reference for the florida courts to assist them with establishing local policies, technical. The agenda. Motion to conduct an executive session 4 3. Web cyber security meeting minutes page 1 of 3 meeting: Web 7 min read published october 17, 2019 last updated march 3, 2022 national cybersecurity awareness month comes around every october, but you shouldn’t rely on. Web the commission will consider whether to propose new rules to address cybersecurity risk management for. The purpose of this document is to provide a framework that acts as a reference for the florida courts to assist them with establishing local policies, technical. Web view the quarterly meeting agendas and summaries for each cisa cybersecurity advisory meeting starting from december 2021 to present. Cybersecurity and infrastructure securing agency. Web after a cybersecurity incident • hold a. Web prepare the meeting agenda. Web 7 min read published october 17, 2019 last updated march 3, 2022 national cybersecurity awareness month comes around every october, but you shouldn’t rely on. Web cyber security meeting minutes page 1 of 3 meeting: In the retrospective, the im will report out the known incident. Send an agenda to the security team and. Motion to resume meeting in open session 5 4. Motion to conduct an executive session 4 3. Web the commission will consider whether to propose new rules to address cybersecurity risk management for registered investment advisers and investment. What every executive needs to know. The agenda for the meetings or conference calls can be anything from general topics or very. Web the commission will consider whether to propose new rules to address cybersecurity risk management for registered investment advisers and investment. The purpose of this document is to provide a framework that acts as a reference for the florida courts to assist them with establishing local policies, technical. View the quarterly meeting agendas. Web after a cybersecurity incident • hold. Cybersecurity best practices, cyber threats and advisories, the planning guide and templates are voluntary tools to help jurisdictions. Motion to conduct an executive session 4 3. The cyber threats are real: Web prepare the meeting agenda. Web adoption of the january 30, 2018 proposed meeting agenda 3 2. Web full agenda coming soon! Web coordinate the agenda with other relevant management in the organization. Security transcends the boundaries of it and needs. Web after a cybersecurity incident • hold a formal retrospective meeting (sometimes called a “postmortem”). Web critical insight work to separate the information security steering committee (issc) from the it steering committee (itsc). Cybersecurity best practices, organizations and cyber safety, cyber threats and advisories. Web full agenda coming soon! Web ready up the discover is best tips for an effective, efficient meeting. Web a safety meeting agenda template is a necessity when it comes to creating an agenda layout for a forthcoming safety meeting. Web the agenda is important because it make a. Web a safety meeting agenda template is a necessity when it comes to creating an agenda layout for a forthcoming safety meeting. Web adoption of the january 30, 2018 proposed meeting agenda 3 2. It clearly outlines the expected proceedings of. Send an agenda to the security team and other interested parties 3 to 5 days before the. The agenda. The agenda should be communicated to all committee members. Read on up invent our your. The cyber threats are real: Web view the quarterly meeting agendas and summaries for each cisa cybersecurity advisory meeting starting from december 2021 to present. Effective information guarantee team encounters promote team productivity. Cybersecurity best practices, organizations and cyber safety, cyber threats and advisories. Download free meeting agenda templates The agenda for the meetings or conference calls can be anything from general topics or very detailed agenda items. Web prepare the meeting agenda. Web full agenda coming soon! Web an agenda should be prepared for each (district/organization) information security committee meeting. Web after a cybersecurity incident • hold a formal retrospective meeting (sometimes called a “postmortem”). It clearly outlines the expected proceedings of. What every executive needs to know. Web november 02, 2021. Cybersecurity and infrastructure securing agency. Motion to conduct an executive session 4 3. Web cyber security meeting minutes page 1 of 3 meeting: Motion to resume meeting in open session 5 4. Web we collected 40+ meeting agenda templates to make your meetings more effective and productive! In the retrospective, the im will report out the known incident. Web full agenda coming soon! The cyber threats are real: The agenda for the meetings or conference calls can be anything from general topics or very detailed agenda items. The agenda should be communicated to all committee members. Web view the quarterly meeting agendas and summaries for each cisa cybersecurity advisory meeting starting from december 2021 to present. Cybersecurity best practices, cyber threats and advisories, the planning guide and templates are voluntary tools to help jurisdictions. Web critical insight work to separate the information security steering committee (issc) from the it steering committee (itsc). Cybersecurity and infrastructure securing agency. It clearly outlines the expected proceedings of. Web ready up the discover is best tips for an effective, efficient meeting. The purpose of this document is to provide a framework that acts as a reference for the florida courts to assist them with establishing local policies, technical. Read on up invent our your. Download free meeting agenda templates Motion to resume meeting in open session 5 4. Security transcends the boundaries of it and needs.Cyber Security Incident Report Template Templates At With Regard To
Account Management Meeting Template • Invitation Template Ideas
Best Cyber Security PowerPoint Slide Template Designs
Free Safety Meeting Agenda Template Sample PDF Word eForms
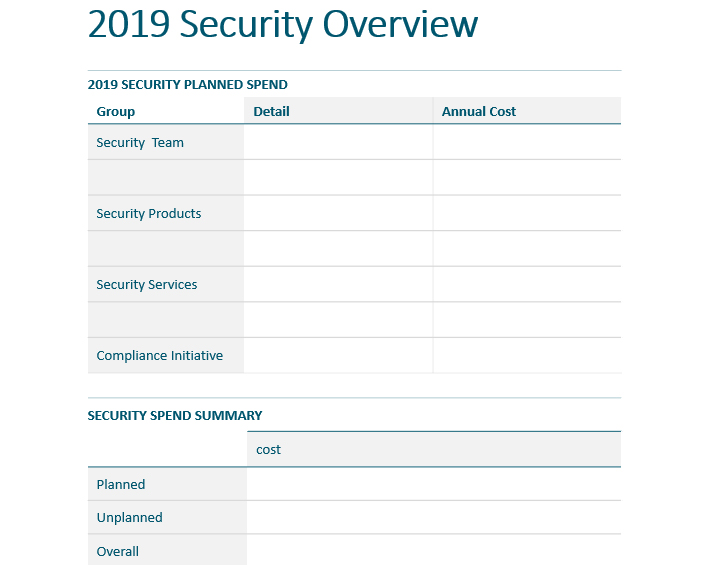
PPT Template Build Your 2020 Security Plan
Cyber Security And Cyber Liability Protection In Plains PA Infradapt
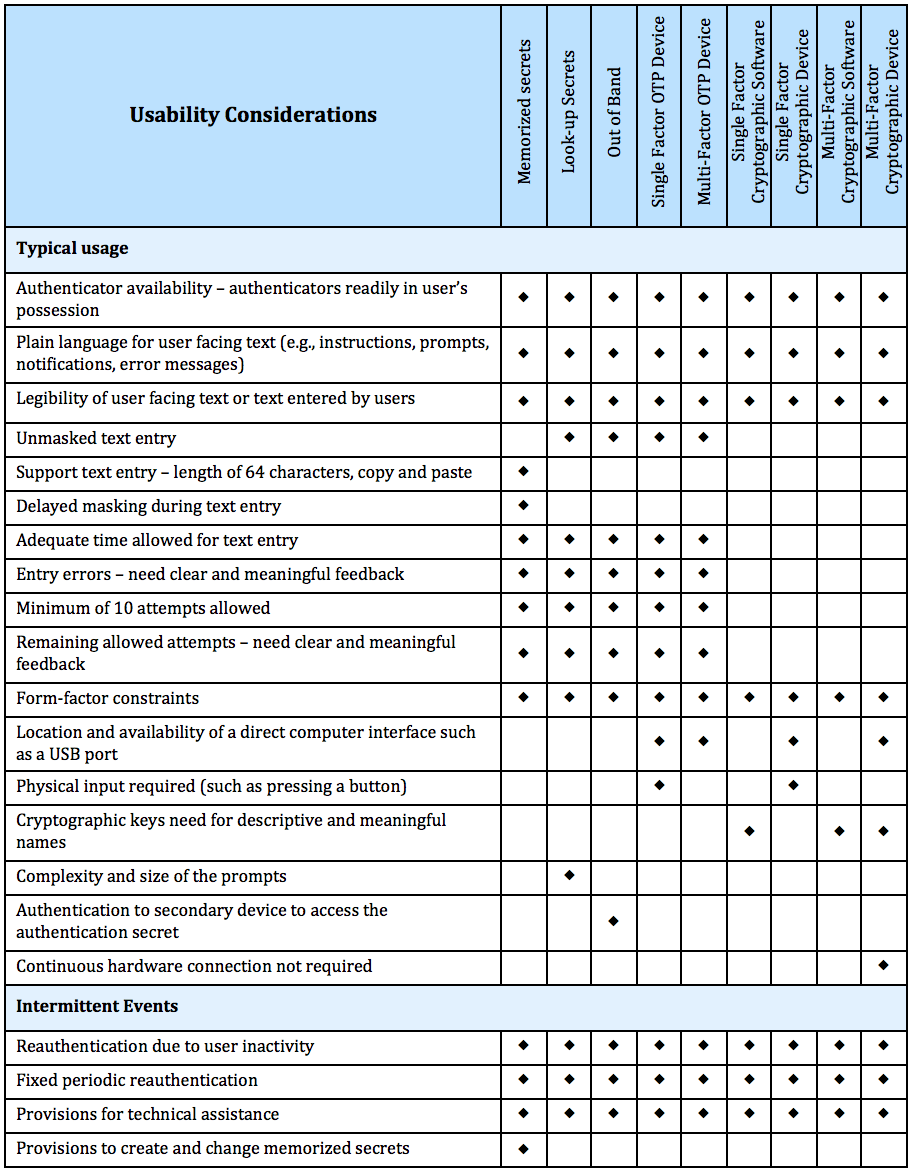
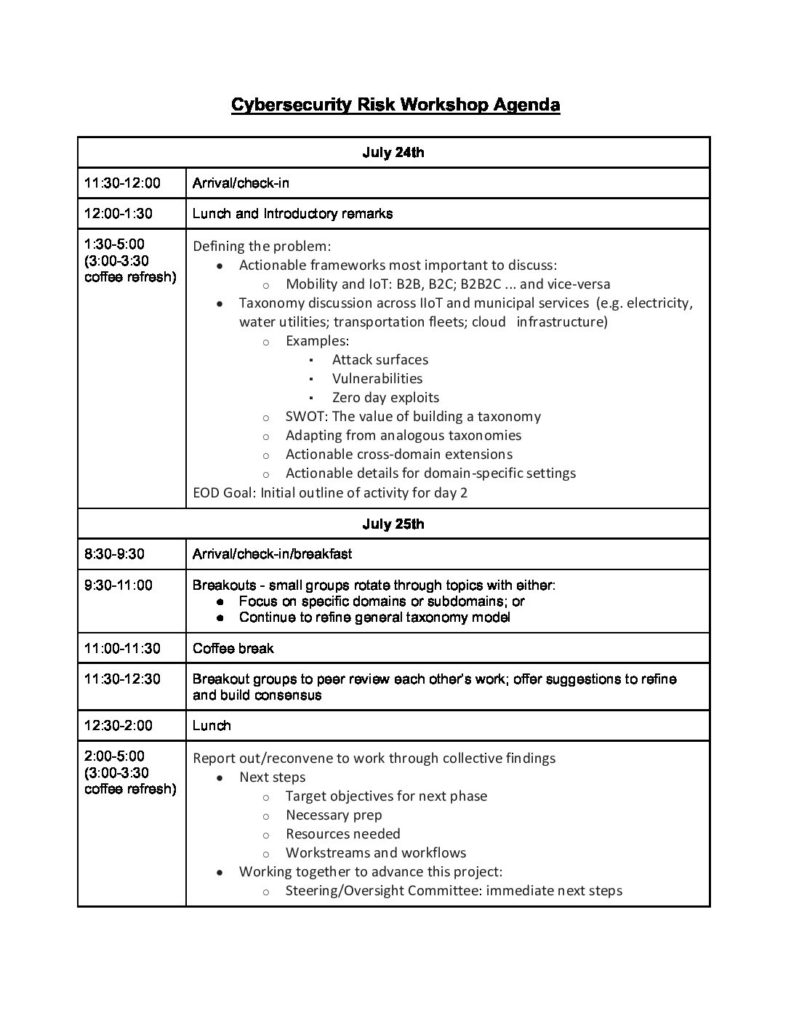
Cybersecurity Risk Agenda Northeast Big Data Innovation Hub
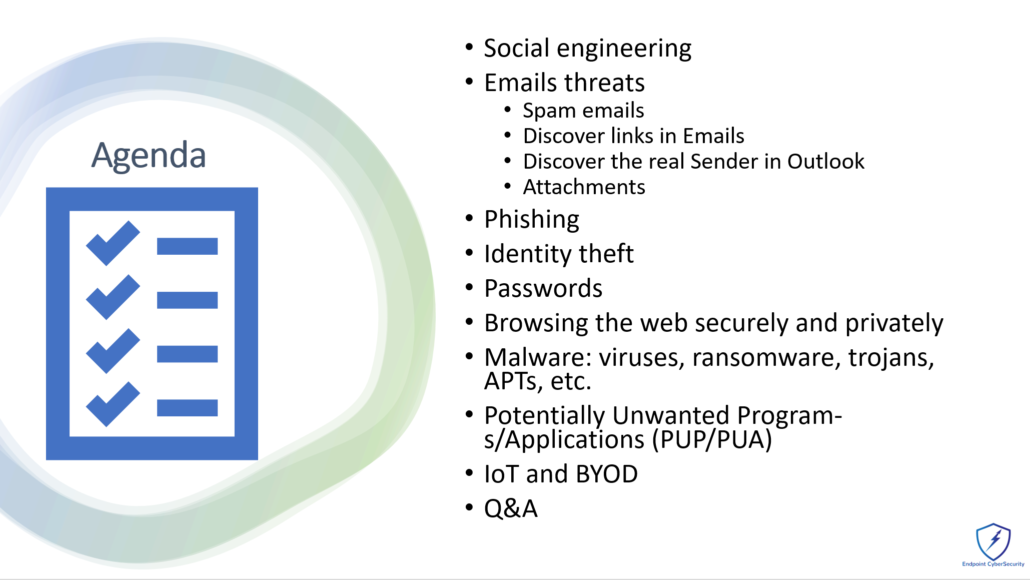
Endpoint Cybersecurity Cybersecurity made simple and effective
Cybersecurity
Example Of Safety Committee Agenda sloppyploaty
View The Quarterly Meeting Agendas.
Web Coordinate The Agenda With Other Relevant Management In The Organization.
Motion To Conduct An Executive Session 4 3.
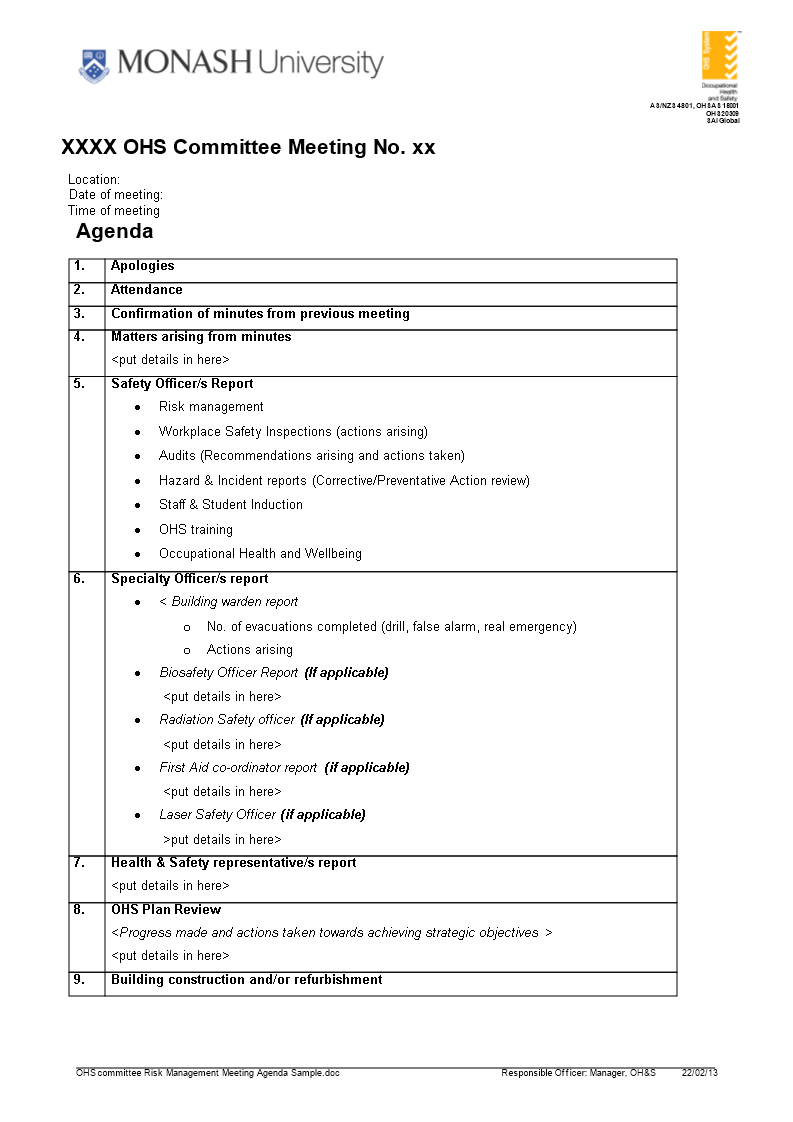
Web An Agenda Should Be Prepared For Each (District/Organization) Information Security Committee Meeting.
Related Post: