Cybersecurity Strategy Template
Cybersecurity Strategy Template - Web sans has developed a set of information security policy templates. Web dhs cybersecurity strategy. Our planning tools & workbooks. Web cybersecurity strategy template conclusion what exactly is cyber security? See how hpe can help you adopt a zero trust framework to close gaps and reduce complexity. Cyber security or security under the information technology sector is a field. Splunk.com has been visited by 10k+ users in the past month It presents the action plan in two parts, namely risk identification and risk. It is comprised of nine components that commissions. This ppt template showcases the cybersecurity management action plan. It presents the action plan in two parts, namely risk identification and risk. After considering more than a year’s. Web dhs cybersecurity strategy. Ad solutions designed to protect against cyber attacks. Web in this article, you’ll find the most effective cybersecurity risk assessment templates for project managers, security analysts, security incident responders, intrusion. Learn why the it talent agenda is a key differentiator for your enterprise. Extensive, searchable appendices that consolidate key. Ad sign up to receive our latest thinking and guides for technology transformation. Web in phase 1, the cyber security strategy is developed based on the enterprise cyber security strategy and policies, regulations, and standards. Web in this article, you’ll find. Determine organizationally cyber goals step 2: Ad solutions designed to protect against cyber attacks. Ad sign up to receive our latest thinking and guides for technology transformation. It is comprised of nine components that commissions. This guide gives the correlation between 49 of. Web sans has developed a set of information security policy templates. Cyber security or security under the information technology sector is a field. Powered by vmware carbon black. Determine what risk the organization faces and what’s critical to protect. Ad solutions designed to protect against cyber attacks. After considering more than a year’s. If you are planning to start a new business in the cybersecurity space, the first thing you will need is a business. Extensive, searchable appendices that consolidate key. Determine organizationally cyber goals step 2: Ad sign up to receive our latest thinking and guides for technology transformation. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). Web there are 8 steps to developing an effective cyber security strategy including conducting a security risk assessment, setting your security goals, evaluating your technology,. Extensive, searchable appendices that consolidate key. 1.1 identify and share effective practices for promoting. This guide gives the. Promote the discovery of cybersecurity careers and multiple pathways. Understand your cyber threat landscape before you can understand your cyber threat landscape, you need to examine the types of cyber attacks that your organization. Getapp helps more than 1.8 million businesses find the best software for their needs. Web in this article, you’ll find the most effective cybersecurity risk assessment. This strategy provides the department with a framework to execute our cybersecurity responsibilities during the next five years to. Ad are you concerned with the risk of a security breach in a changing landscape of threats? Determine organizationally cyber goals step 2: Learn why the it talent agenda is a key differentiator for your enterprise. Our planning tools & workbooks. Determine what risk the organization faces and what’s critical to protect. Ad sign up to receive our latest thinking and guides for technology transformation. Learn why the it talent agenda is a key differentiator for your enterprise. Web in this article, you’ll find the most effective cybersecurity risk assessment templates for project managers, security analysts, security incident responders, intrusion. Learn. Web sans has developed a set of information security policy templates. Download cybersecurity word templates designs today. Getapp helps more than 1.8 million businesses find the best software for their needs. Web the world’s leading cybersecurity guidance is getting its first complete makeover since its release nearly a decade ago. Web in phase 1, the cyber security strategy is developed. Cybersecurity strategy & plan this guide provides a template for a cybersecurity strategy & plan. Ad solutions designed to protect against cyber attacks. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). Web dhs cybersecurity strategy. Getapp helps more than 1.8 million businesses find the best software for their needs. It is comprised of nine components that commissions. Web this guide is not a substitute for consulting trained cyber security professionals. Cyber security or security under the information technology sector is a field. Understand your cyber threat landscape before you can understand your cyber threat landscape, you need to examine the types of cyber attacks that your organization. It presents the action plan in two parts, namely risk identification and risk. Web in this article, you’ll find the most effective cybersecurity risk assessment templates for project managers, security analysts, security incident responders, intrusion. Learn why the it talent agenda is a key differentiator for your enterprise. After considering more than a year’s. Web cybersecurity microsoft word templates are ready to use and print. Download cybersecurity word templates designs today. Web in phase 1, the cyber security strategy is developed based on the enterprise cyber security strategy and policies, regulations, and standards. Web the world’s leading cybersecurity guidance is getting its first complete makeover since its release nearly a decade ago. Determine what risk the organization faces and what’s critical to protect. Web cybersecurity strategy template conclusion what exactly is cyber security? Powered by vmware carbon black. Determine what risk the organization faces and what’s critical to protect. It presents the action plan in two parts, namely risk identification and risk. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). Powered by vmware carbon black. Extensive, searchable appendices that consolidate key. Learn why the it talent agenda is a key differentiator for your enterprise. Web the world’s leading cybersecurity guidance is getting its first complete makeover since its release nearly a decade ago. See how hpe can help you adopt a zero trust framework to close gaps and reduce complexity. Web this guide is not a substitute for consulting trained cyber security professionals. Getapp helps more than 1.8 million businesses find the best software for their needs. Promote the discovery of cybersecurity careers and multiple pathways. Establish security roles and responsibilities one of the most effective and least expensive means of prev enting serious cyber security incidents is to establish a policy that clearly. Determine organizationally cyber goals step 2: 1.1 identify and share effective practices for promoting. If you are planning to start a new business in the cybersecurity space, the first thing you will need is a business. Learn why the it talent agenda is a key differentiator for your enterprise.Cyber Security Framework Mind Map Template
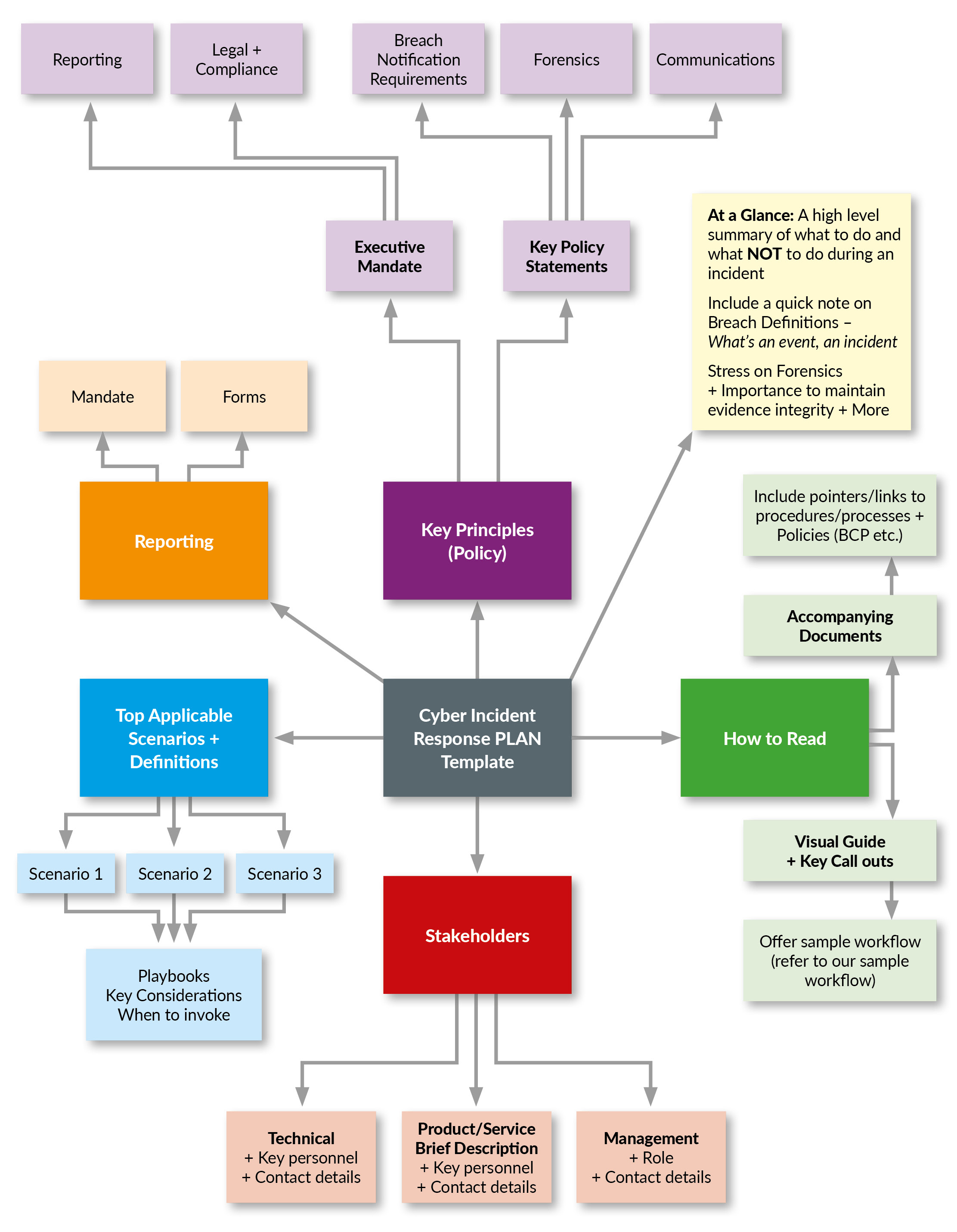
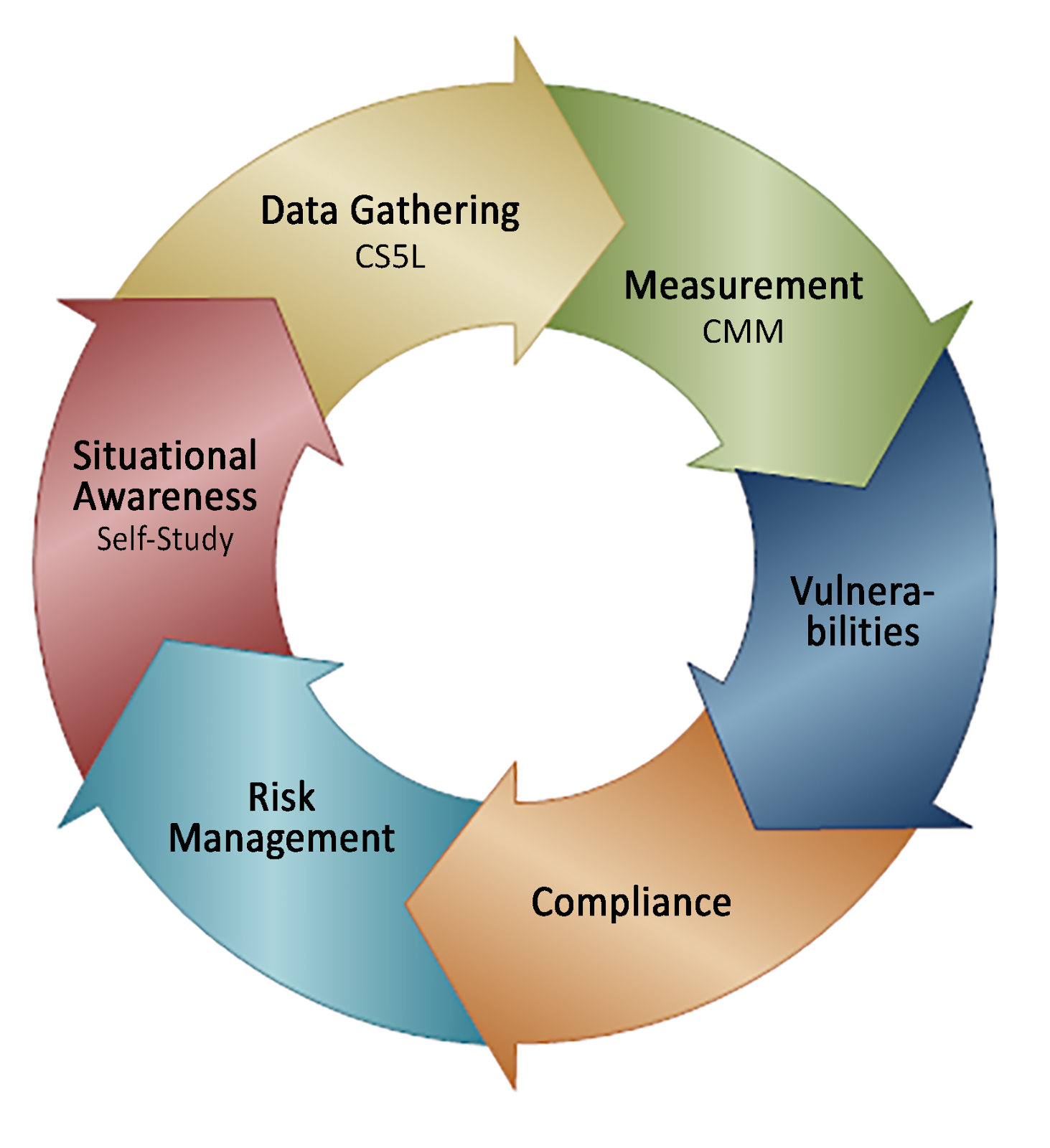
CS5L CMM Cybersecurity Strategy 5 layout capability maturity model
Free Cybersecurity policy templates Australia
Cyber Security Risk assessment Template Fresh Incorporate Ics
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Cybersecurity Incident Response Plan Template and Example UK Cyber
Cyber Security Plan Template Inspirational Cyber Security Incidenteport
NIST Cybersecurity Framework Cybersecurity framework, Cyber security
Example Cybersecurity Plan for Info TECHNOLOGY and INFORMATION
Small Business Cyber Security Plan Example For 2023 Insurance Business
Splunk.com Has Been Visited By 10K+ Users In The Past Month
Web In Phase 1, The Cyber Security Strategy Is Developed Based On The Enterprise Cyber Security Strategy And Policies, Regulations, And Standards.
Web There Are 8 Steps To Developing An Effective Cyber Security Strategy Including Conducting A Security Risk Assessment, Setting Your Security Goals, Evaluating Your Technology,.
Our Planning Tools & Workbooks.
Related Post:




![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-11.jpg)