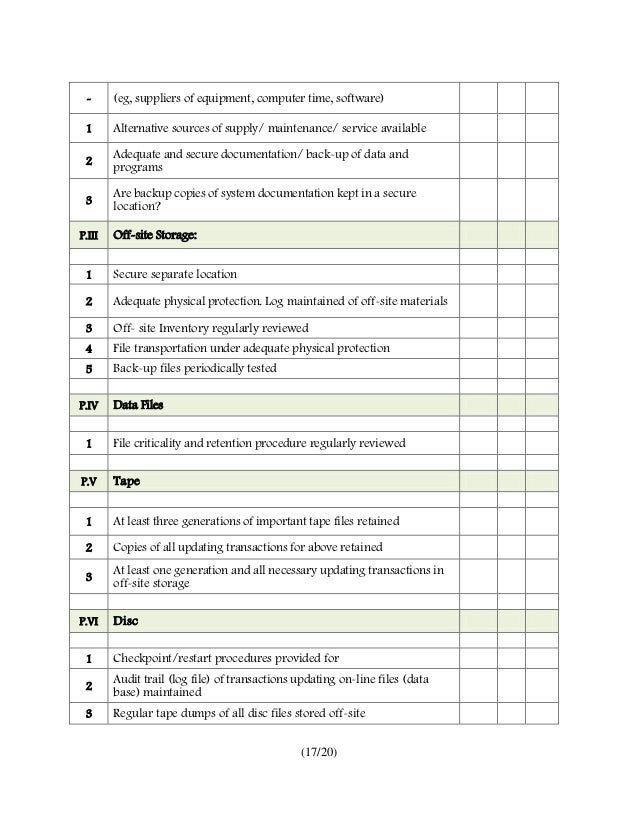
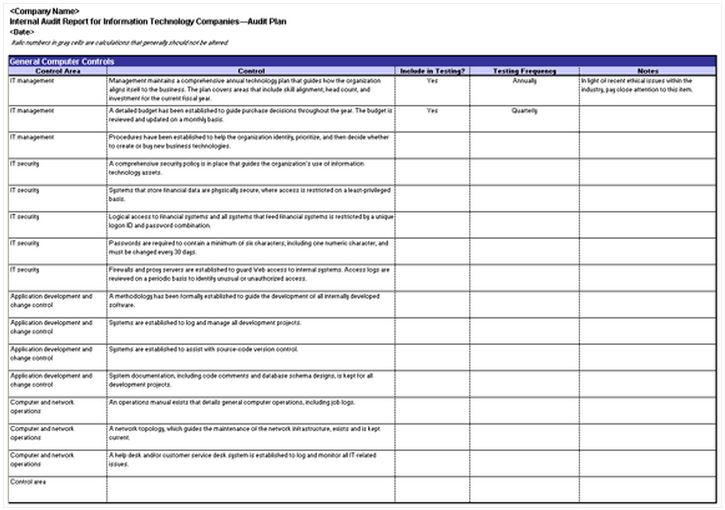
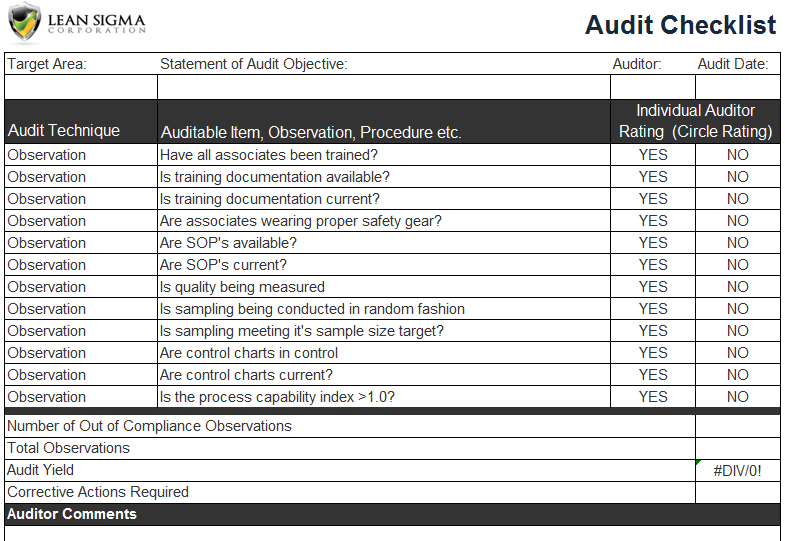
Network Security Checklist Template
Network Security Checklist Template - 11.2.4 equipment maintenance defined policy for equipment maintenance? Hpe can help you secure your data infrastructure and protect against ransomware attacks. Web proactively maintain web security by conducting network security assessments using customizable network audit checklists: 11.2.5 removal of assets defined policy for. Understand which threats to look for 5. Settle on the audit’s scope 4. Use this risk assessment template specifically designed for it and network security. Decide on the necessary tools or personnel 2. Web pdf template, a network security audit checklist is used to proactively assess the security and integrity of organizational networks. Web network security audit checklist. Web learn the keys components of ampere network security audit audit, also how to make sure your network has secure. This guide gives the correlation between 49 of. Hpe can help you secure your data infrastructure and protect against ransomware attacks. It managers and network security. Sonarsource.com has been visited by 10k+ users in the past month Use this risk assessment template specifically designed for it and network security. Examples of the checklist are also included. Web network security audit checklist. Web this process street network security audit checklist is engineered to be used to assist a risk manager or equivalent it professional in assessing a network for security. 11.2.5 removal of assets defined policy for. Settle on the audit’s scope 4. By alex strickland on jan 1, 2012. Understand which threats to look for 5. Web network security checklist: Verify the existing network security policy 3. Sonarsource.com has been visited by 10k+ users in the past month Web in this post, we share with you a network security checklist of action items and security best practices that illustrate how you can secure your business network. Scores 4.81 with 384 votes. Web titanhq can provide you with a template for creating your own network security checklist and. General a written network security policy that lists the rights and responsibilities of all staff, employees, and consultants security training for all users regarding the use of the. Enter as many vulnerabilities observed as needed and fill out the fields, attach optional photos or flow diagrams, and provide the risk rating and recommend. Enter your details here to find out.. Web network security audit checklist. Enter as many vulnerabilities observed as needed and fill out the fields, attach optional photos or flow diagrams, and provide the risk rating and recommend. Understand which threats to look for 5. Web network security checklist: Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). Use this risk assessment template specifically designed for it and network security. Settle on the audit’s scope 4. Sonarsource.com has been visited by 10k+ users in the past month General a written network security policy that lists the rights and responsibilities of all staff, employees, and consultants security training for all users regarding the use of the. Web network security. Web proactively maintain web security by conducting network security assessments using customizable network audit checklists: Verify the existing network security policy 3. Web this article contains information about what a network security checklist is, as well as steps on improving your network security. Web this process street network security audit checklist is engineered to be used to assist a risk. Web proactively maintain web security by conducting network security assessments using customizable network audit checklists: Web in this post, we share with you a network security checklist of action items and security best practices that illustrate how you can secure your business network. Use this risk assessment template specifically designed for it and network security. Web a thorough policy will. Use this risk assessment template specifically designed for it and network security. Web network security risk assessment template. Examples of the checklist are also included. Sonarsource.com has been visited by 10k+ users in the past month Settle on the audit’s scope 4. Web proactively maintain web security by conducting network security assessments using customizable network audit checklists: Web this process street network security audit checklist is engineered to be used to assist a risk manager or equivalent it professional in assessing a network for security. Hpe can help you secure your data infrastructure and protect against ransomware attacks. 11.2.5 removal of assets defined policy for. It managers and network security. Web network security checklist. Enter as many vulnerabilities observed as needed and fill out the fields, attach optional photos or flow diagrams, and provide the risk rating and recommend. Web a thorough policy will cover topics such as: Web network security audit checklist. Web pdf template, a network security audit checklist is used to proactively assess the security and integrity of organizational networks. Web titanhq can provide you with a template for creating your own network security checklist and hardening your network against threats. Web this article contains information about what a network security checklist is, as well as steps on improving your network security. Verify the existing network security policy 3. Decide on the necessary tools or personnel 2. Web customize safetyculture network security audit templates to fit the demands of owner organization. Sonarsource.com has been visited by 10k+ users in the past month This guide gives the correlation between 49 of. Ad are you concerned with the risk of a security breach in a changing landscape of threats? Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). Understand which threats to look for 5. Decide on the necessary tools or personnel 2. Ad data enrichment to reduce false positives & add context to alerts | powerful automation. Web customize safetyculture network security audit templates to fit the demands of owner organization. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). 11.2.4 equipment maintenance defined policy for equipment maintenance? This guide gives the correlation between 49 of. 11.2.5 removal of assets defined policy for. Scores 4.81 with 384 votes. General a written network security policy that lists the rights and responsibilities of all staff, employees, and consultants security training for all users regarding the use of the. Web network security checklist. Web this article contains information about what a network security checklist is, as well as steps on improving your network security. By alex strickland on jan 1, 2012. Enter as many vulnerabilities observed as needed and fill out the fields, attach optional photos or flow diagrams, and provide the risk rating and recommend. Settle on the audit’s scope 4. Use this risk assessment template specifically designed for it and network security. Web this process street network security audit checklist is engineered to be used to assist a risk manager or equivalent it professional in assessing a network for security.Physical Security Checklist Template Fresh 27 Of Network Security
Security Audit Network Security Audit Checklist Pdf
Get Our Image of Security Assessment Checklist Template for Free
Network Assessment Checklist Access Control Password
Checklist for Network Devices Security Developers & Agencies
√ Free Printable IT Security Checklist Template Checklist Templates
Security Audit Network Security Audit Checklist Pdf
Security Audit Network Security Audit Checklist Excel
Database Security Checklist Template Database security, Checklist
Explore Our Example of Security Assessment Checklist Template for Free
Web In This Post, We Share With You A Network Security Checklist Of Action Items And Security Best Practices That Illustrate How You Can Secure Your Business Network.
Understand Which Threats To Look For 5.
Web A Thorough Policy Will Cover Topics Such As:
Ad Are You Concerned With The Risk Of A Security Breach In A Changing Landscape Of Threats?
Related Post: