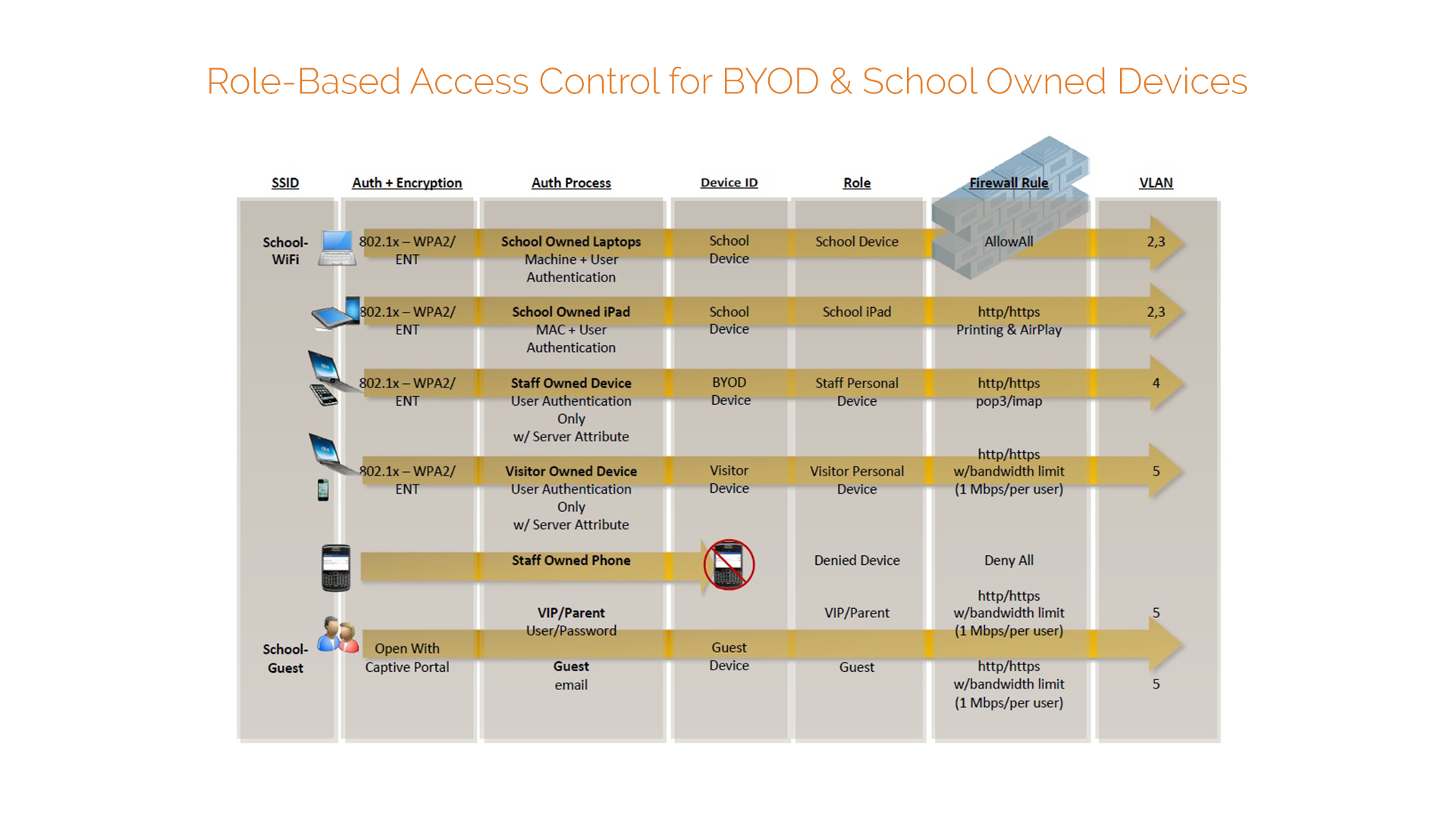
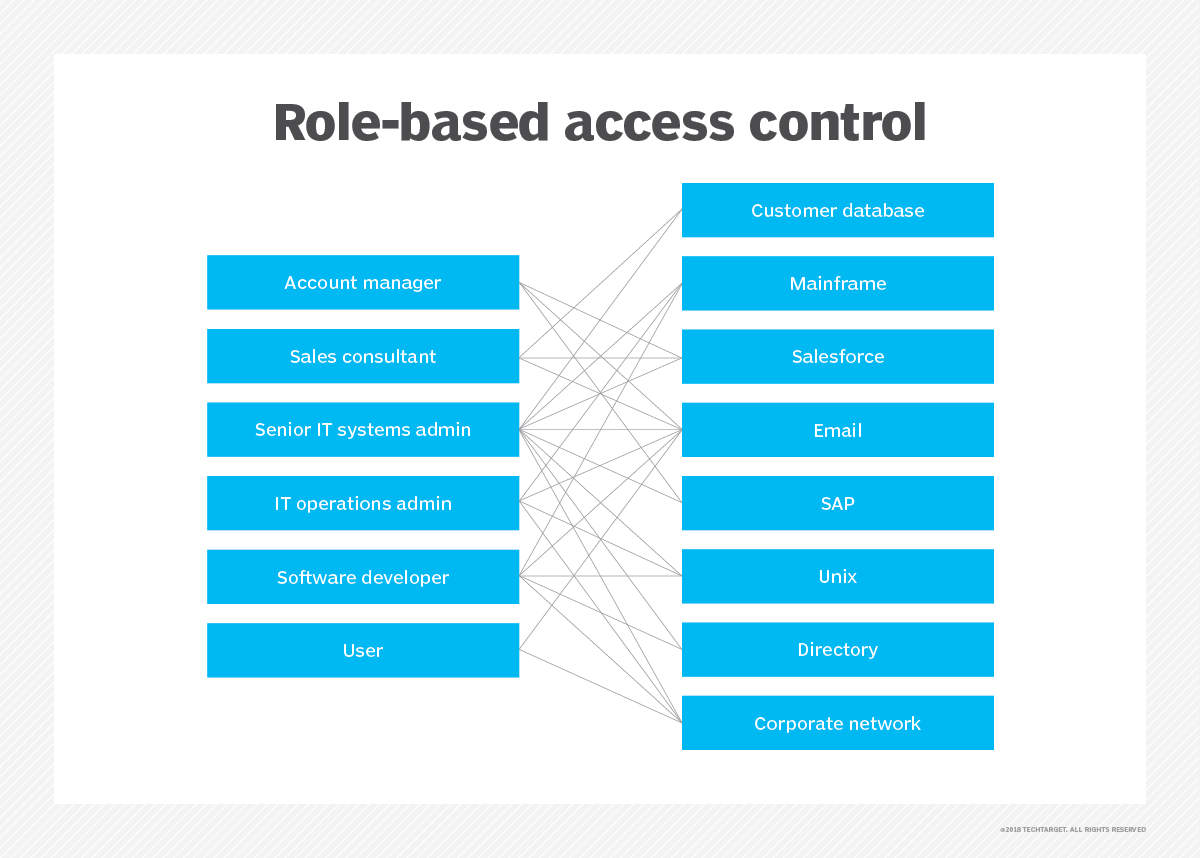
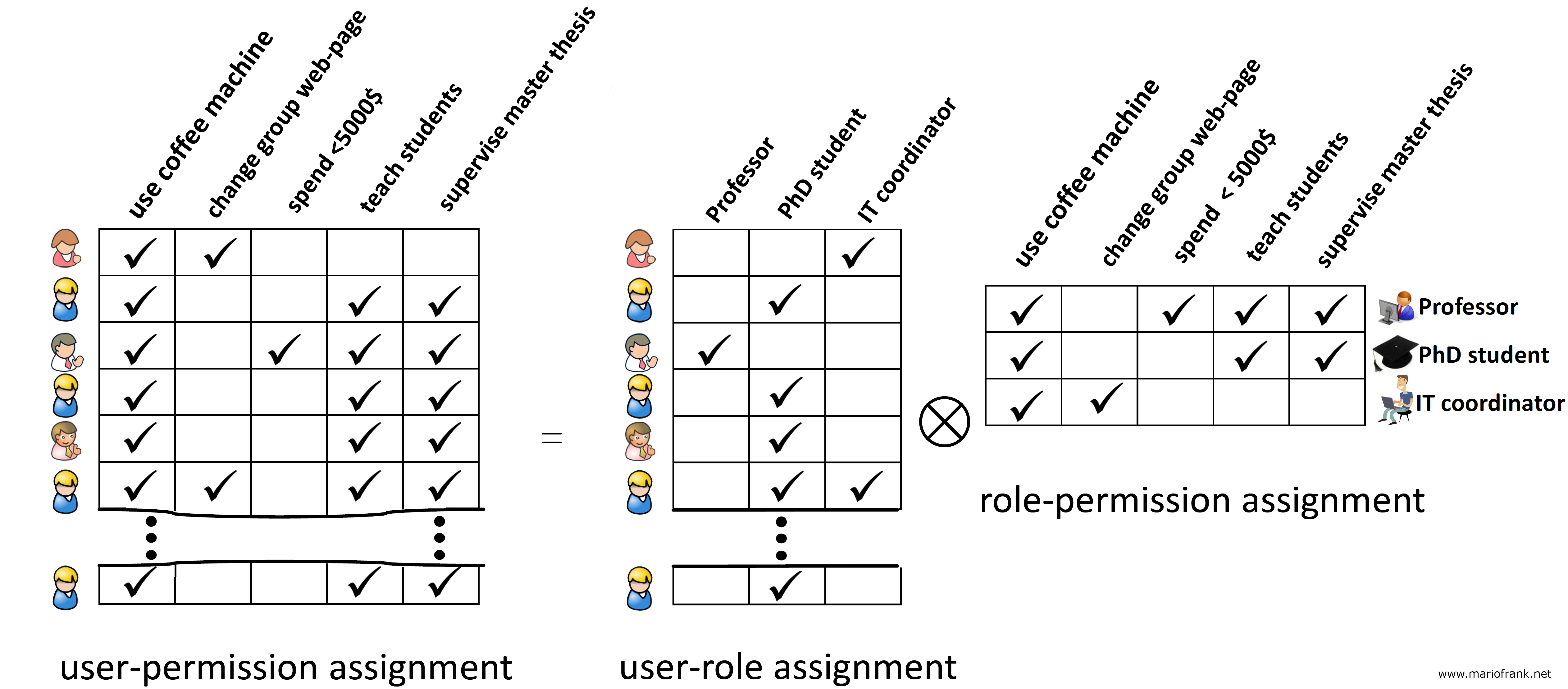
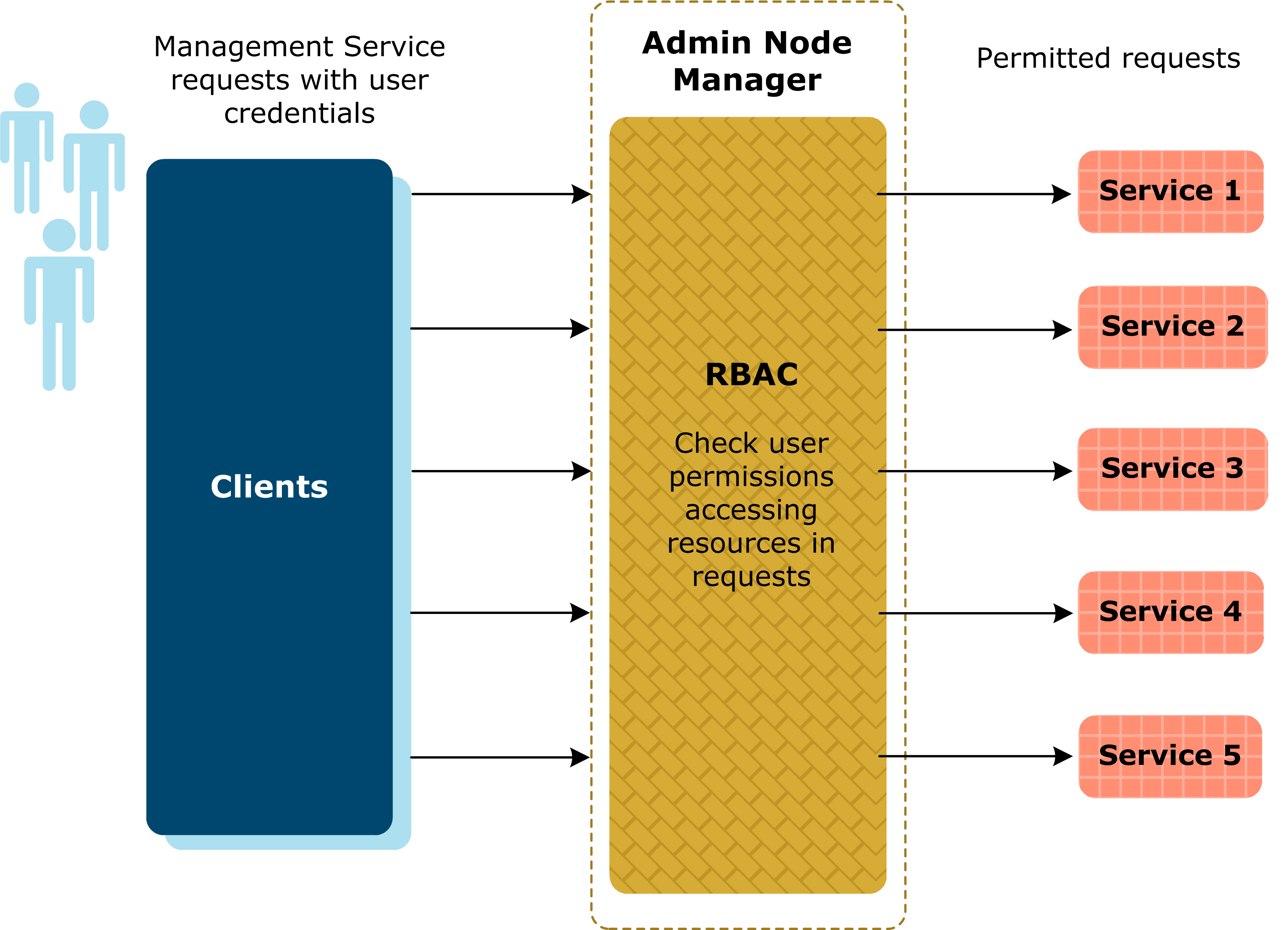
Rbac Matrix Template
Rbac Matrix Template - In this quickstart, you create a resource group and grant a. This is a free responsibility assignment matrix (ram) template in excel and opendocument spreadsheet. Web a security analyst will benefit from the use of an rbac matrix. Project management tool in excel. This clickup role based control. Web this report focuses on an rbac model originally proposed by ferraiolo and others at nist, and formulates a revised model that fixes noted discrepancies,. Web access control matrix • list all proceses and files in a matrix • each row is a process (“subject”) • each column is a file (“object”). Web using an excel template for a raci matrix enhances its effectiveness by providing a structured format that can be easily customized and shared among project. The way you control access to resources using azure rbac is to assign azure roles. The rbac tf will use role engineering models to assist it in carrying out its activities. Web 5 role engineering models. These best practices are derived from our experience. Web # what is rbac and how to design for it? Web rbac is a method of regulating access to resources (protected objects) based on the roles of individual users within a system. Web how azure rbac works. Web how azure rbac works. This is a free responsibility assignment matrix (ram) template in excel and opendocument spreadsheet. The template is fully editable with. Using rbac • rbac is the mechanism of. Web 5 role engineering models. The requirements traceability matrix (rtm) is a tool to help ensure that the project's scope. Project management tool in excel. Using rbac • rbac is the mechanism of. Web a security analyst will benefit from the use of an rbac matrix. Web rbac is an access control mechanism which: This clickup role based control. Web # what is rbac and how to design for it? The template is fully editable with. Web ready govern show 5 more the cloud adoption framework has tools, templates, and assessments that can help you quickly implement technical changes. After reviewing the scenario in the module four activity. Web rbac is a method of regulating access to resources (protected objects) based on the roles of individual users within a system. In this context, access is the ability of an individual. Web using an excel template for a raci matrix enhances its effectiveness by providing a structured format that can be easily customized and shared among project. For instance,. The requirements traceability matrix (rtm) is a tool to help ensure that the project's scope. In this quickstart, you create a resource group and grant a. Web a security analyst will benefit from the use of an rbac matrix. The rbac tf will use role engineering models to assist it in carrying out its activities. The way you control access. The way you control access to resources using azure rbac is to assign azure roles. These best practices are derived from our experience. Web ready govern show 5 more the cloud adoption framework has tools, templates, and assessments that can help you quickly implement technical changes. Web a security analyst will benefit from the use of an rbac matrix. Web. Web rbac is a method of regulating access to resources (protected objects) based on the roles of individual users within a system. For instance, under rbac, a. The template is fully editable with. Web role based access control (rbac) is a new approach to controlling user access to different features of a software application or website. These best practices are. After reviewing the scenario in the module four activity. Web access control matrix • list all proceses and files in a matrix • each row is a process (“subject”) • each column is a file (“object”). Web how azure rbac works. In this quickstart, you create a resource group and grant a. It offers protection by allowing people to have. Web 5 role engineering models. Web a security analyst will benefit from the use of an rbac matrix. Using rbac • rbac is the mechanism of. The way you control access to resources using azure rbac is to assign azure roles. Project management tool in excel. The template is fully editable with. This is a free responsibility assignment matrix (ram) template in excel and opendocument spreadsheet. In this context, access is the ability of an individual. Web # what is rbac and how to design for it? Web access control matrix • list all proceses and files in a matrix • each row is a process (“subject”) • each column is a file (“object”). Using rbac • rbac is the mechanism of. Create, assign and manage tasks & responsibilities. Models illustrate relationships between components of an. Web how azure rbac works. For instance, under rbac, a. After reviewing the scenario in the module four activity. In this quickstart, you create a resource group and grant a. These best practices are derived from our experience. Web a security analyst will benefit from the use of an rbac matrix. Web this report focuses on an rbac model originally proposed by ferraiolo and others at nist, and formulates a revised model that fixes noted discrepancies,. This clickup role based control. Web rbac is an access control mechanism which: The way you control access to resources using azure rbac is to assign azure roles. Web 5 role engineering models. Project management tool in excel. Web 5 role engineering models. The template is fully editable with. After reviewing the scenario in the module four activity. Web rbac is a method of regulating access to resources (protected objects) based on the roles of individual users within a system. Models illustrate relationships between components of an. Web how azure rbac works. Web # what is rbac and how to design for it? It offers protection by allowing people to have just the permissions they need to do their job. Web this report focuses on an rbac model originally proposed by ferraiolo and others at nist, and formulates a revised model that fixes noted discrepancies,. Web rbac is an access control mechanism which: Create, assign and manage tasks & responsibilities. Using rbac • rbac is the mechanism of. Web access control matrix • list all proceses and files in a matrix • each row is a process (“subject”) • each column is a file (“object”). In this context, access is the ability of an individual. Web a security analyst will benefit from the use of an rbac matrix. The rbac tf will use role engineering models to assist it in carrying out its activities.RoleBased Access Control What is It, and What are the Benefits?
5 Document Control Template Excel Excel Templates
What is RBAC? Definition from TechTarget News ITN
Mario Frank
RoleBased Access Control (RBAC) CyberHoot
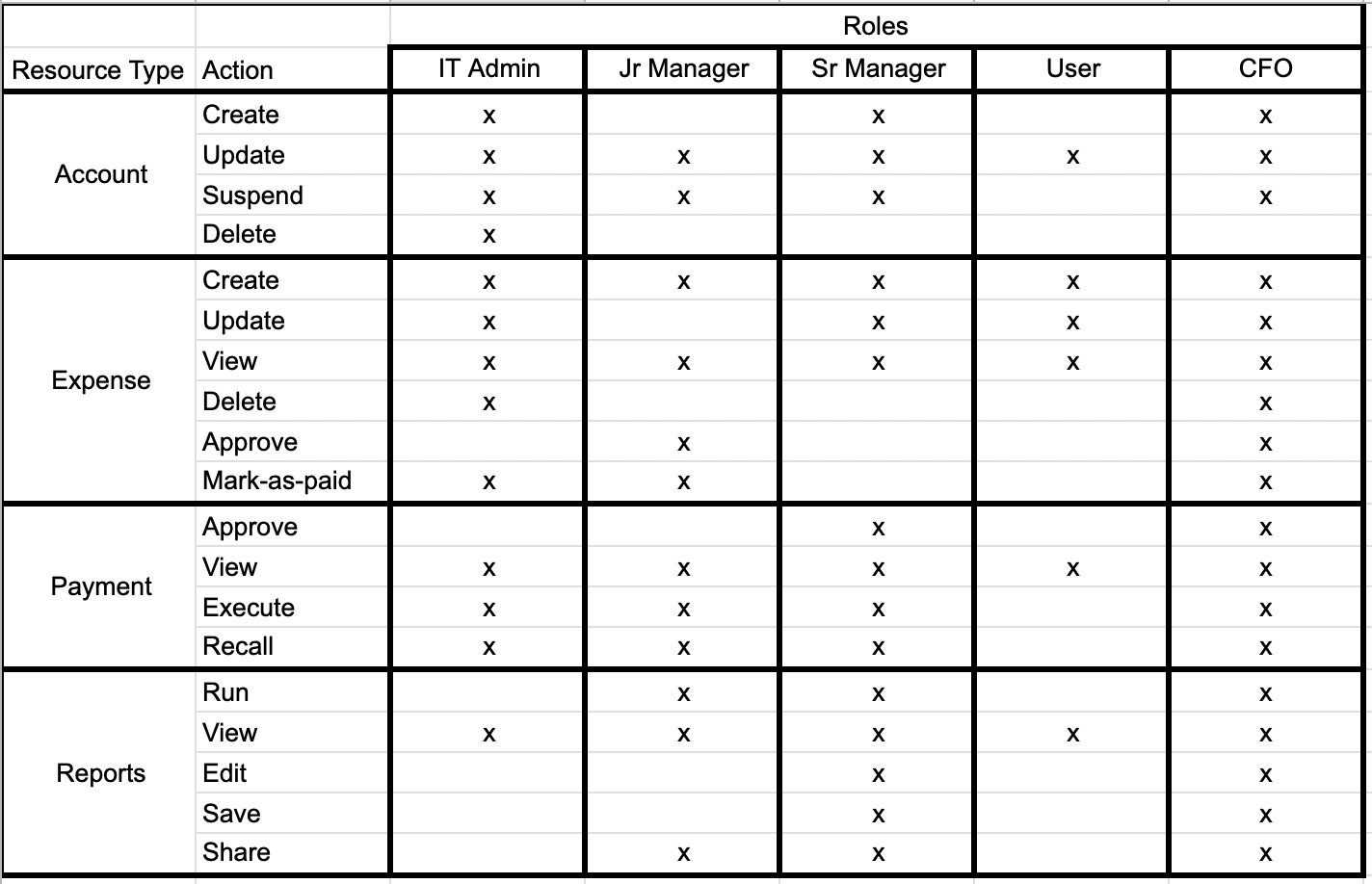
Rbac Model Avoid Role Based Access Control Pitfalls By Bala Dutt
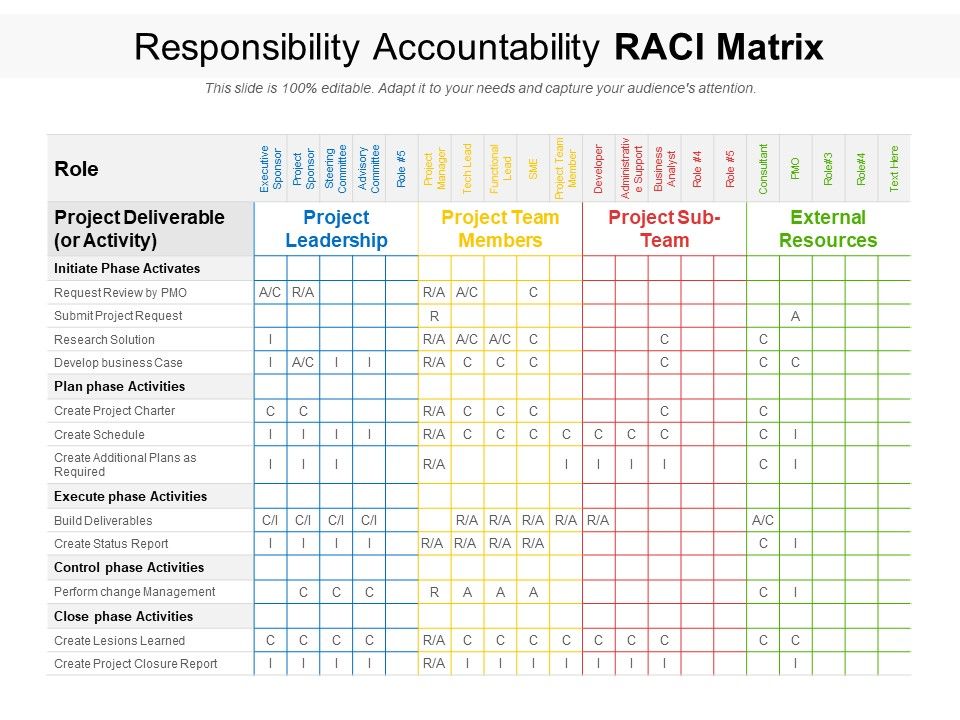
Responsibility Accountability RACI Matrix PowerPoint Presentation
RBAC (Role Based Access Control) in EAP 6.2 Part I Not Another IT Blog
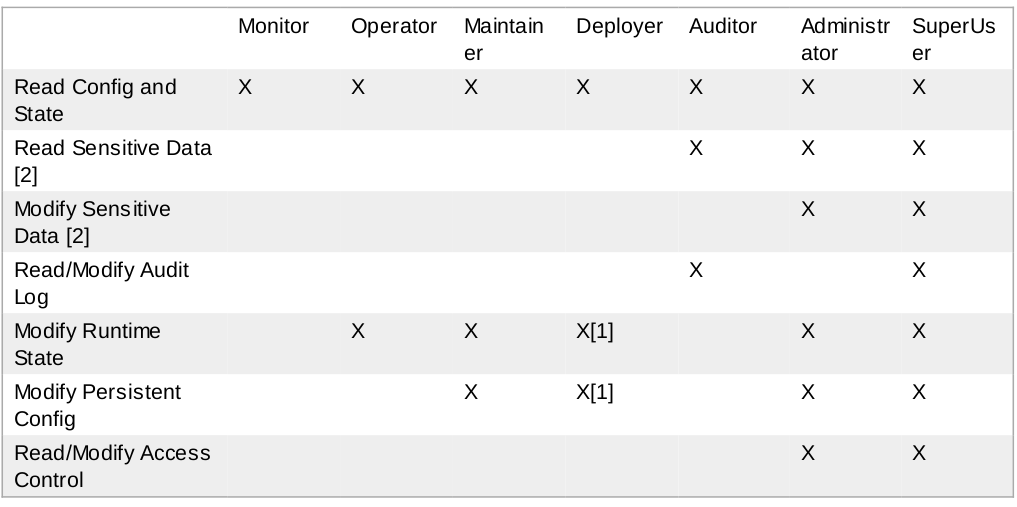
Mapping business requirements to authorization policy
RoleBased Access Control (RBAC). RoleBased Access Control (RBAC) by
The Way You Control Access To Resources Using Azure Rbac Is To Assign Azure Roles.
Web Using An Excel Template For A Raci Matrix Enhances Its Effectiveness By Providing A Structured Format That Can Be Easily Customized And Shared Among Project.
Web Role Based Access Control (Rbac) Is A New Approach To Controlling User Access To Different Features Of A Software Application Or Website.
In This Quickstart, You Create A Resource Group And Grant A.
Related Post: