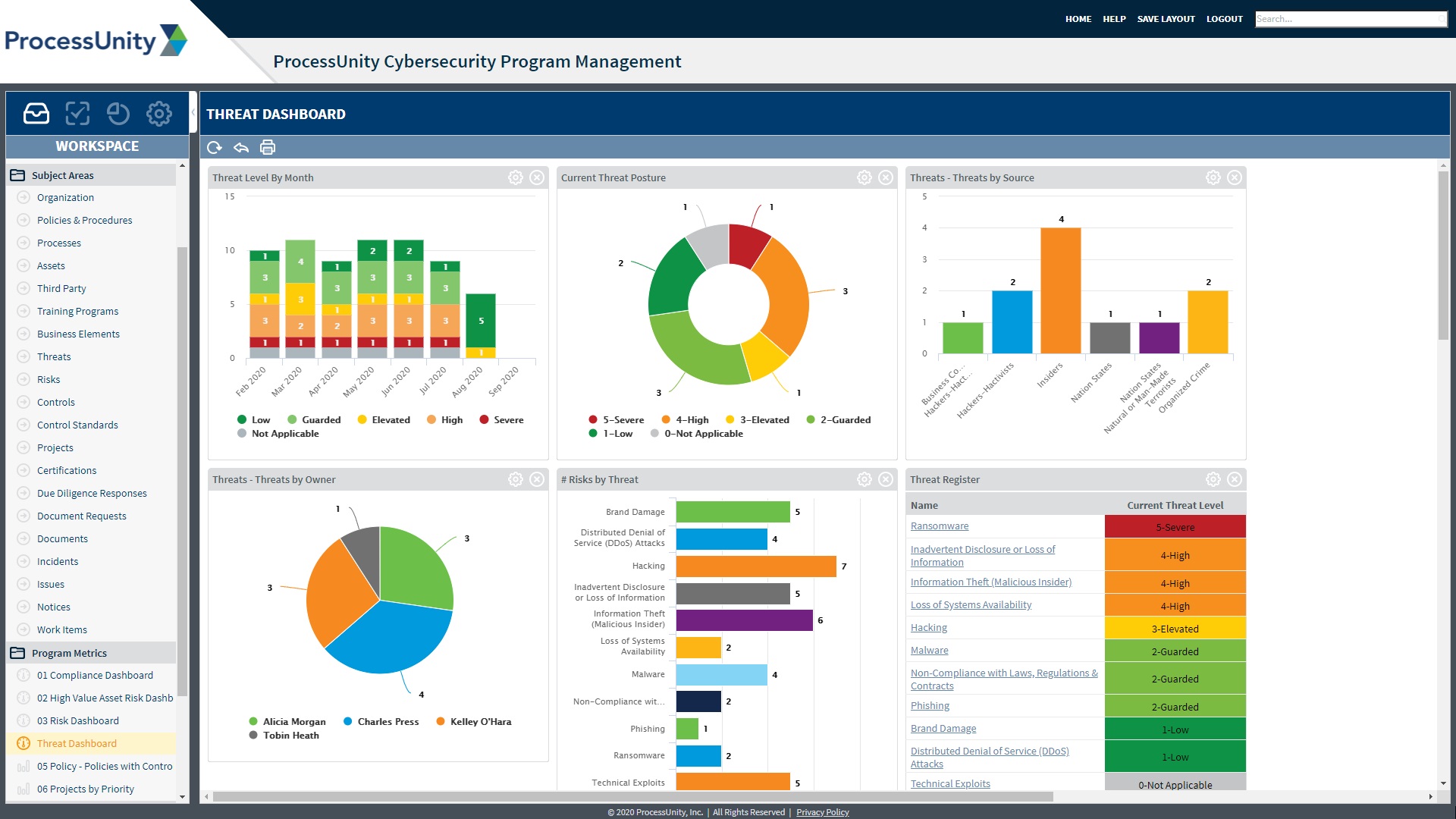
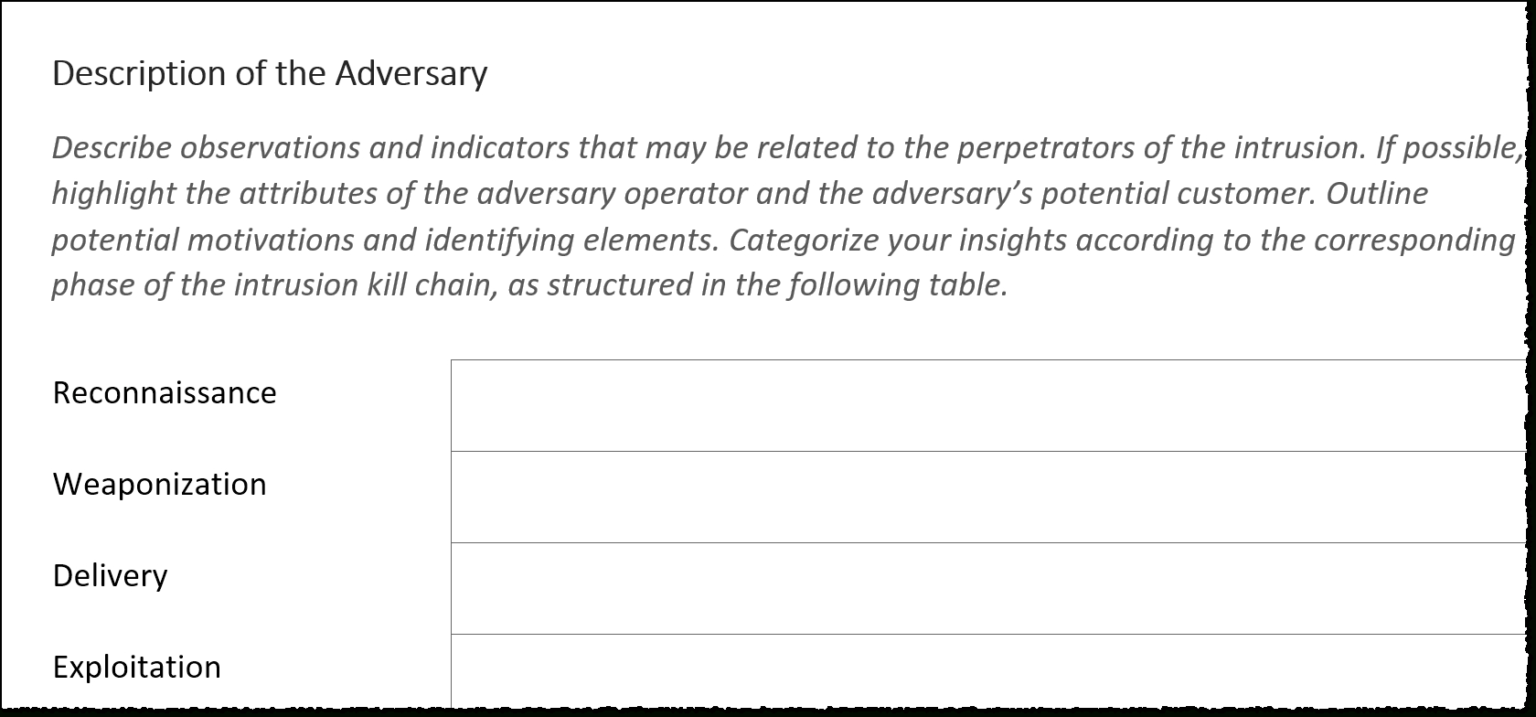
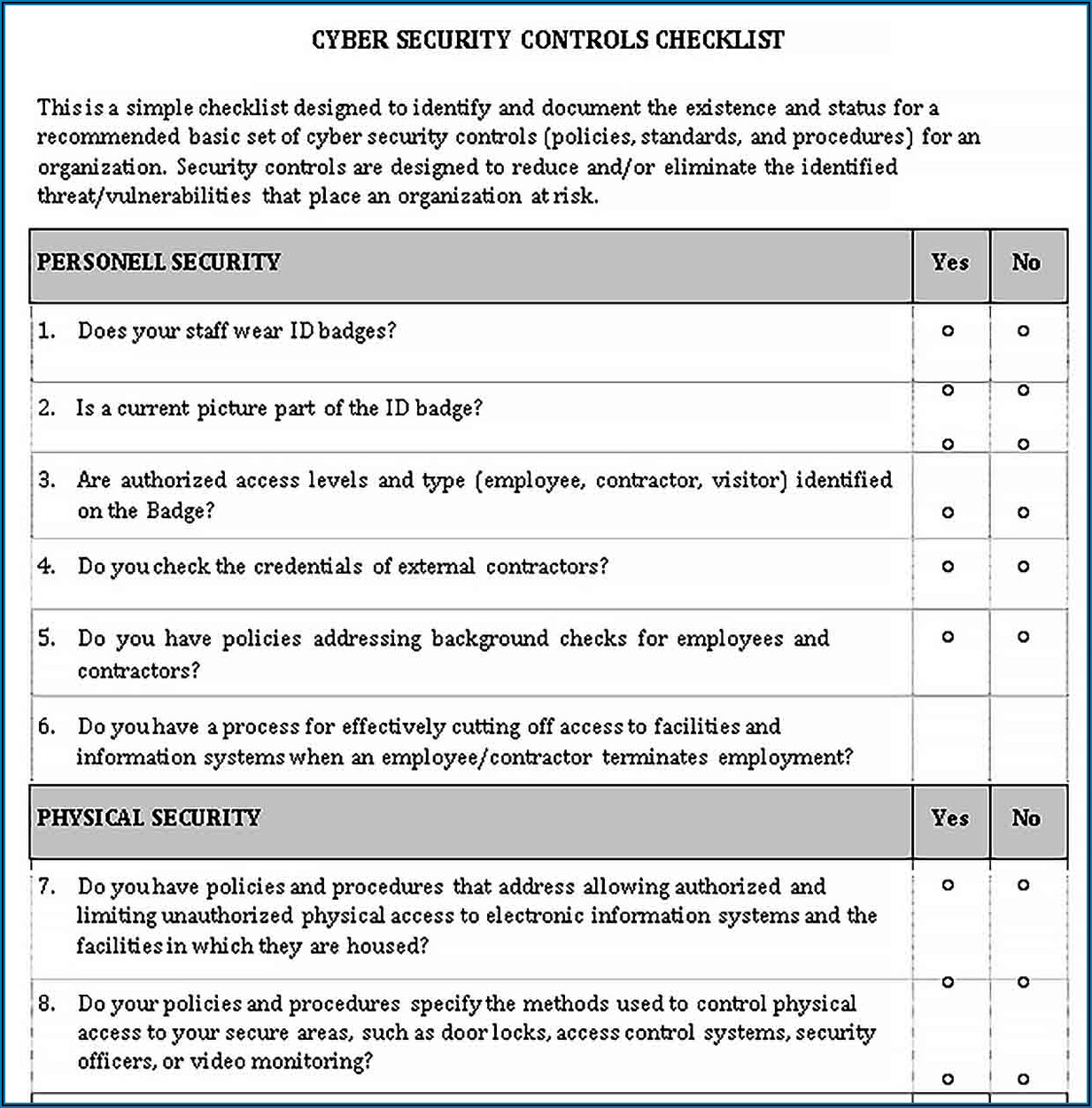
Threat Intelligence Report Template
Threat Intelligence Report Template - Web this template leverages several models in the cyber threat intelligence domain (such as the intrusion kill chain, campaign correlation, the courses of action matrix and the. Get set up in minutes with1st reporting, invite your team and begin reporting. Ad tired of complex and expensive reporting systems? Web in this blog, katie shares strategies, tools, and frameworks for building an effective threat intelligence team. To unlock the full content, please fill out our simple form and receive instant access. Set a direction the first step in this process is to set the direction of your program, meaning you need to outline what you're looking for and what questions you. I am going to show you what iso 27001:2022 annex a 5.7 threat intelligence is, what’s new, give you iso 27001 templates, show you examples, do a walkthrough. Web the purpose of this threat assessment report is to provide clear picture on the potential threats that are most likely to happen if they are not mitigated in the early stages. Web although there’s no single template for crafting a threat report, “it should look like whatever you think people will read,” says degrazia. M /d y d i stri b u ti on : The suite includes templates for executive,. Set a direction the first step in this process is to set the direction of your program, meaning you need to outline what you're looking for and what questions you. Web a threat analysis report is a document that summarizes the findings and recommendations of a threat assessment process. Web although there’s no single. Web threat intelligence reports (tirs) are an important tool for businesses looking to stay informed about the latest cyber threats and take appropriate actions to. Web justify the threat intelligence initiative to management by customizing the following sections: Web templates empower intelligence teams to create actionable, repeatable reports tailored to specific audiences. Web although there’s no single template for crafting. Detect threats and generate security. Set a direction the first step in this process is to set the direction of your program, meaning you need to outline what you're looking for and what questions you. I am going to show you what iso 27001:2022 annex a 5.7 threat intelligence is, what’s new, give you iso 27001 templates, show you examples,. Web in this blog, katie shares strategies, tools, and frameworks for building an effective threat intelligence team. It helps organizations identify and. The suite includes templates for executive,. Web although there’s no single template for crafting a threat report, “it should look like whatever you think people will read,” says degrazia. Web view and manage the imported threat intelligence in. Week of [month, day, year] published on: Where should cyber threat intelligence. I am going to show you what iso 27001:2022 annex a 5.7 threat intelligence is, what’s new, give you iso 27001 templates, show you examples, do a walkthrough. Detect threats and generate security. Web a threat analysis report is a document that summarizes the findings and recommendations of. Web threat intelligence templates this is a set of templates based on the templates created in sapho to help track and share cyber threat intelligence using open source. Web templates empower intelligence teams to create actionable, repeatable reports tailored to specific audiences. Web in this blog, katie shares strategies, tools, and frameworks for building an effective threat intelligence team. Set. Web justify the threat intelligence initiative to management by customizing the following sections: I am going to show you what iso 27001:2022 annex a 5.7 threat intelligence is, what’s new, give you iso 27001 templates, show you examples, do a walkthrough. S h a r e a b le — c a n b e sh a r ed w. M /d y d i stri b u ti on : Set a direction the first step in this process is to set the direction of your program, meaning you need to outline what you're looking for and what questions you. The suite includes templates for executive,. Web nsa keeps you aware of evolving cyber threats by offering the following. Web in this blog, katie shares strategies, tools, and frameworks for building an effective threat intelligence team. Web nsa keeps you aware of evolving cyber threats by offering the following downloadable products. The suite includes templates for executive,. Web the purpose of this threat assessment report is to provide clear picture on the potential threats that are most likely to. Web templates empower intelligence teams to create actionable, repeatable reports tailored to specific audiences. Week of [month, day, year] published on: Detect threats and generate security. Web nsa keeps you aware of evolving cyber threats by offering the following downloadable products. Get set up in minutes with1st reporting, invite your team and begin reporting. Web in this blog, katie shares strategies, tools, and frameworks for building an effective threat intelligence team. To unlock the full content, please fill out our simple form and receive instant access. Get set up in minutes with1st reporting, invite your team and begin reporting. Web although there’s no single template for crafting a threat report, “it should look like whatever you think people will read,” says degrazia. Week of [month, day, year] published on: Web a threat analysis report is a document that summarizes the findings and recommendations of a threat assessment process. Set a direction the first step in this process is to set the direction of your program, meaning you need to outline what you're looking for and what questions you. Ad tired of complex and expensive reporting systems? Web this template leverages several models in the cyber threat intelligence domain (such as the intrusion kill chain, campaign correlation, the courses of action matrix and the. S h a r e a b le — c a n b e sh a r ed w i th cl i en t a n d p r osp ects ex e c u ti v. Web justify the threat intelligence initiative to management by customizing the following sections: The suite includes templates for executive,. It helps organizations identify and. Detect threats and generate security. Web threat intelligence management plan template. Web templates empower intelligence teams to create actionable, repeatable reports tailored to specific audiences. Web view and manage the imported threat intelligence in logs and in the threat intelligence blade of microsoft sentinel. Web the purpose of this threat assessment report is to provide clear picture on the potential threats that are most likely to happen if they are not mitigated in the early stages. M /d y d i stri b u ti on : Web threat intelligence reports (tirs) are an important tool for businesses looking to stay informed about the latest cyber threats and take appropriate actions to. Week of [month, day, year] published on: Web a threat analysis report is a document that summarizes the findings and recommendations of a threat assessment process. M /d y d i stri b u ti on : Web view and manage the imported threat intelligence in logs and in the threat intelligence blade of microsoft sentinel. The suite includes templates for executive,. S h a r e a b le — c a n b e sh a r ed w i th cl i en t a n d p r osp ects ex e c u ti v. Ad tired of complex and expensive reporting systems? Web threat intelligence templates this is a set of templates based on the templates created in sapho to help track and share cyber threat intelligence using open source. Set a direction the first step in this process is to set the direction of your program, meaning you need to outline what you're looking for and what questions you. To unlock the full content, please fill out our simple form and receive instant access. Get set up in minutes with1st reporting, invite your team and begin reporting. Web the purpose of this threat assessment report is to provide clear picture on the potential threats that are most likely to happen if they are not mitigated in the early stages. Web threat intelligence reports (tirs) are an important tool for businesses looking to stay informed about the latest cyber threats and take appropriate actions to. It helps organizations identify and. Web nsa keeps you aware of evolving cyber threats by offering the following downloadable products. I am going to show you what iso 27001:2022 annex a 5.7 threat intelligence is, what’s new, give you iso 27001 templates, show you examples, do a walkthrough.Cybersecurity Program Management ProcessUnity
Bomb Threat Report form (Free and editable template)
FREE 10+ Sample Threat Assessments in PDF M Word
Ir Report Template (5) TEMPLATES EXAMPLE
Report Template For Threat Intelligence And Incident Response
Threat Assessment Report Template (5) PROFESSIONAL TEMPLATES
Cyber Security Incident Report Template Word Template 1 Resume
sample cyber threat intelligence report TEMPLATES EXAMPLE
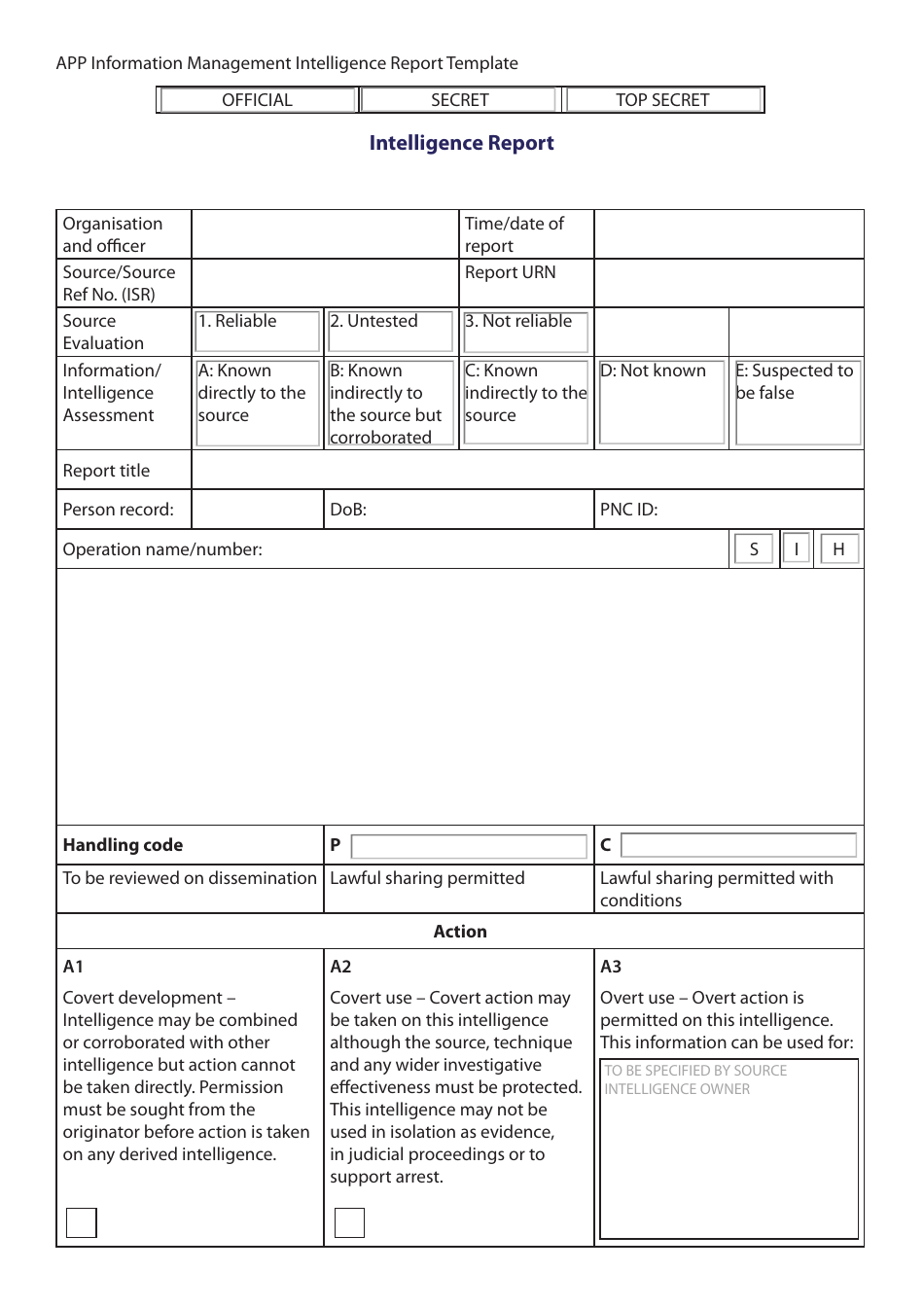
Intelligence Report Template College of Policing Download Fillable
How to foster mental health resilience and engage in self care with
Where Should Cyber Threat Intelligence.
Web Although There’s No Single Template For Crafting A Threat Report, “It Should Look Like Whatever You Think People Will Read,” Says Degrazia.
Web Templates Empower Intelligence Teams To Create Actionable, Repeatable Reports Tailored To Specific Audiences.
Web Threat Intelligence Management Plan Template.
Related Post: