Web Application Security Policy Template
Web Application Security Policy Template - Companies rely on them to communicate with partners, clients, shareholders and others,. Save 100s of hours / month. Web 7+ application security policy templates; Rocketlawyer.com has been visited by 100k+ users in the past month Managing signature, server technologies, and browser. Build security features into your sdlc w/ 50+ integrations. Web web application firewall policies contain all the waf settings and configurations. Web overview it's scary out there for developers! Web this application security policy template includes the following sections: 4 what should a security policy template contain? Web sans has developed a set of information security policy templates. Web web application firewall policies contain all the waf settings and configurations. Ad maximize performance, find vulnerabilities, and minimize false positives. Web 5 rows rapid deployment policy (rdp) a moderate protection layer that includes manual learning of false. Web create a security policy for a web application by having. Web sans has developed a set of information security policy templates. Web overview it's scary out there for developers! Web open web application security project (owasp) and owasp secure coding guidelines will be followed. Web dan virgillito web applications are critical to the enterprise infrastructure. Web the following defines and details the generic policy templates you can submit for creating. Web this application security policy template includes the following sections: Web use a template to populate the attributes of a new web application security policy. Web 1 security policy templates; Web introduction the materials presented in this document are obtained from the open web application security project (owasp), the sans (sysadmin, audit, network,. Web dan virgillito web applications are critical. Web this template creates a front door standard/premium including a web application firewall with a custom rule. Web 1 security policy templates; Build security features into your sdlc w/ 50+ integrations. One mistake in the code, one vulnerability in a dependency, one compromised developer workstation, and your. Default policy statements that define what the enterprise must do. One mistake in the code, one vulnerability in a dependency, one compromised developer workstation, and your. Save 100s of hours / month. 3 information security policy templates; Web use a template to populate the attributes of a new web application security policy. These are free to use and fully customizable to your company's it security practices. Web 1 security policy templates; 3 information security policy templates; Managing signature, server technologies, and browser. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). This includes exclusions, custom rules, managed rules, and so on. Build security features into your sdlc w/ 50+ integrations. 2 types of security policy templates; Policy templates allow you to reduce the time required to configure a policy for your. Web web application firewall policies contain all the waf settings and configurations. Navigate to the policy templates screen, configuration security web application security policy templates a list of all policy. Save 100s of hours / month. These are free to use and fully customizable to your company's it security practices. Web application security assessments must be performed to identify potential or realized weaknesses (e.g., insecure coding, inadvertent misconfiguration,. Build security features into your sdlc. 2 types of security policy templates; 3 information security policy templates; Web 5 rows rapid deployment policy (rdp) a moderate protection layer that includes manual learning of false. Web application security assessments must be performed to identify potential or realized weaknesses (e.g., insecure coding, inadvertent misconfiguration,. Office of information security (ois) will establish the required controls. Web web application firewall policies contain all the waf settings. This guide gives the correlation between 49 of. Build security features into your sdlc. Office of information security (ois) will establish the required controls. Web application security assessments must be performed to identify potential or realized weaknesses (e.g., insecure coding, inadvertent misconfiguration,. Build security features into your sdlc w/ 50+ integrations. Web overview it's scary out there for developers! This guide gives the correlation between 49 of. Build security features into your sdlc w/ 50+ integrations. Ad maximize performance, find vulnerabilities, and minimize false positives. Configuring web application security logging. Ad maximize performance, find vulnerabilities, and minimize false positives. Build security features into your sdlc. Build security features into your sdlc. One mistake in the code, one vulnerability in a dependency, one compromised developer workstation, and your. Web web application security policy templates. Managing signature, server technologies, and browser. Web open web application security project (owasp) and owasp secure coding guidelines will be followed. Companies rely on them to communicate with partners, clients, shareholders and others,. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). Over 1000 companies trust acunetix with their web application vulnerability testing. Save 100s of hours / month. Web 7+ application security policy templates; Web this application security policy template includes the following sections: Web web application firewall policies contain all the waf settings and configurations. Web the following defines and details the generic policy templates you can submit for creating a new web applications security raise or baby policy ( shape security web. Navigate to the policy templates screen, configuration security web application security policy templates a list of all policy templates are displayed. Web open web application security project (owasp) and owasp secure coding guidelines will be followed. Web web application security policy templates. Web use a template to populate the attributes of a new web application security policy. Web sans has developed a set of information security policy templates. Managing signature, server technologies, and browser. Web create a security policy for a web application by having the system examine traffic and create the policy based on statistical analysis of the traffic and the intended behavior of. Build security features into your sdlc w/ 50+ integrations. Create azure front door in front of azure api. Office of information security (ois) will establish the required controls. Web dan virgillito web applications are critical to the enterprise infrastructure. It is a fixed policy that only. Rocketlawyer.com has been visited by 100k+ users in the past month One mistake in the code, one vulnerability in a dependency, one compromised developer workstation, and your. This includes exclusions, custom rules, managed rules, and so on. Configuring web application security logging.Policy Template 10+ Free Word, PDF Document Downloads
Website Security Policy Template For Your Needs
Pci Dss Information Security Policy Template Template 2 Resume
Free Cyber Security Policy Template Of 42 Information Security Policy
Pin on Example Application Form Templates
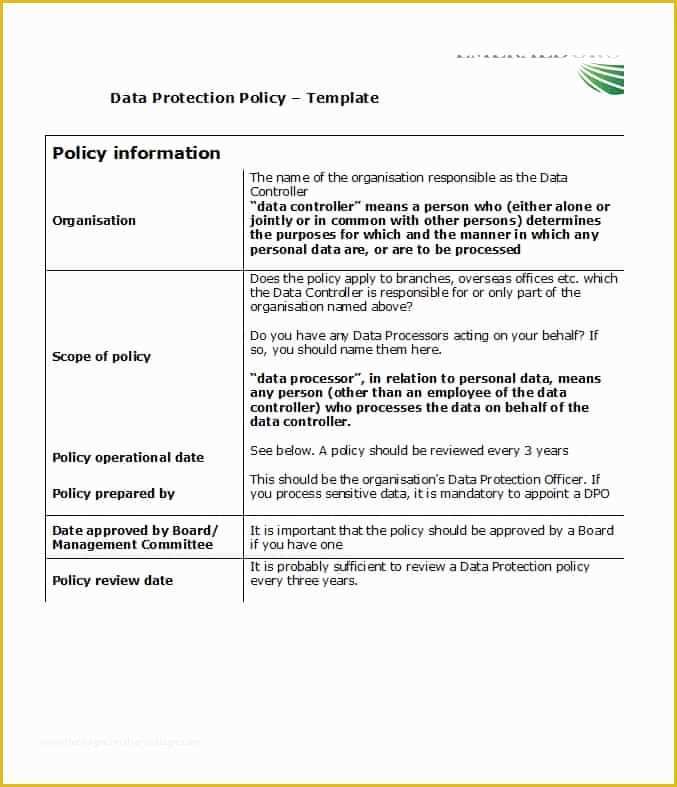
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
20+ Free Information Security Policy Templates [Word, PDF] » TemplateData
It Security Policy Template Free Printable Templates
Jobsite Security Policy Template Master of Documents
Information Security Policy Template Addictionary
Build Security Features Into Your Sdlc.
These Are Free To Use And Fully Customizable To Your Company's It Security Practices.
Web Web Application Firewall Policies Contain All The Waf Settings And Configurations.
This Guide Gives The Correlation Between 49 Of.
Related Post:





![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-06.jpg)
![20+ Free Information Security Policy Templates [Word, PDF] » TemplateData](https://templatedata.net/wp-content/uploads/2021/07/intranet-and-internet-security-policy-template.jpg)


